hack.lu CTF 2019 Writeup
Contents
URL: https://fluxfingersforfuture.fluxfingers.net/challenges/
以下は、チャレンジ一覧です。
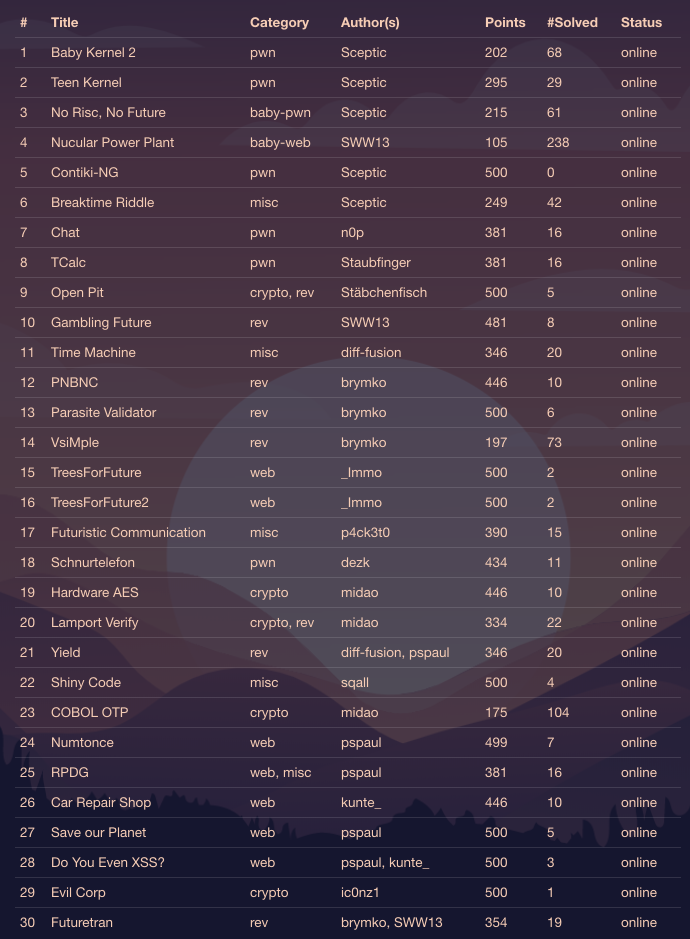
平日だったこともあり、17番のmisc問題だけトライしました。
実は、解けてないですが、なんとなく方向性はあってる気がするのでWriteup残しておきます。
[Misc]: Futuristic Communication
Challenge
Communication in the future is a big thing. With the rising amount of data in the internet new handshake techniques are required. Here is my implementation, where I can identify who did request which resources.
Remark: The remote host in the PCAPs is not the host you have to connect to.
Note: Because we use network protocols in a very futuristic way, you should check your network setup like firewall or router if you have problems solving this challenge. Maybe it’s easier for you to use a cloud provider.
Announcements for Futuristic Communication
(Published on 2019-10-23 02:08:22)
Because we use network protocols in a very futuristic way, you should check your network setup like firewall or router if you have problems solving this challenge. Maybe it’s easier for you to use a cloud provider.
(Published on 2019-10-22 16:56:08)
Due to high load the server may sometimes have difficulty keeping up with processing identifiers which may cause the package to be dropped. Please insert a delay of about 1-2 seconds before sending a package containing an identifier to ensure those packages will be processed.
Attachments:
- futuristic_communication.pcapng
Unsolved
まずは、Wiresharkでpcapを開いて、Follow TCP Streamします。
Welcome to handshake in future!
Your personal identifier is: 051733e3-ec47-4518-9ff9-9ec90af9b27b
Waiting for identification, on TCP port 13792
Identification successful. Waiting for further instructions.
Expecting handshake, on TCP port 38462, with sequence number 2339380618
Connection setup noticed. Your Commands:
synchronize
privileged
flag
All your TCP flags should be SYN flags.
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
synchronize... success
Check if the connection is synchronized.
Connection synchronized. Entering privileged mode.
flag{only-to-show-now-comes-flag}
“tcp.port==13792” でフィルターすると、受け取った personal identifier を SYNパケットにくっつけて送っているのが見えます。
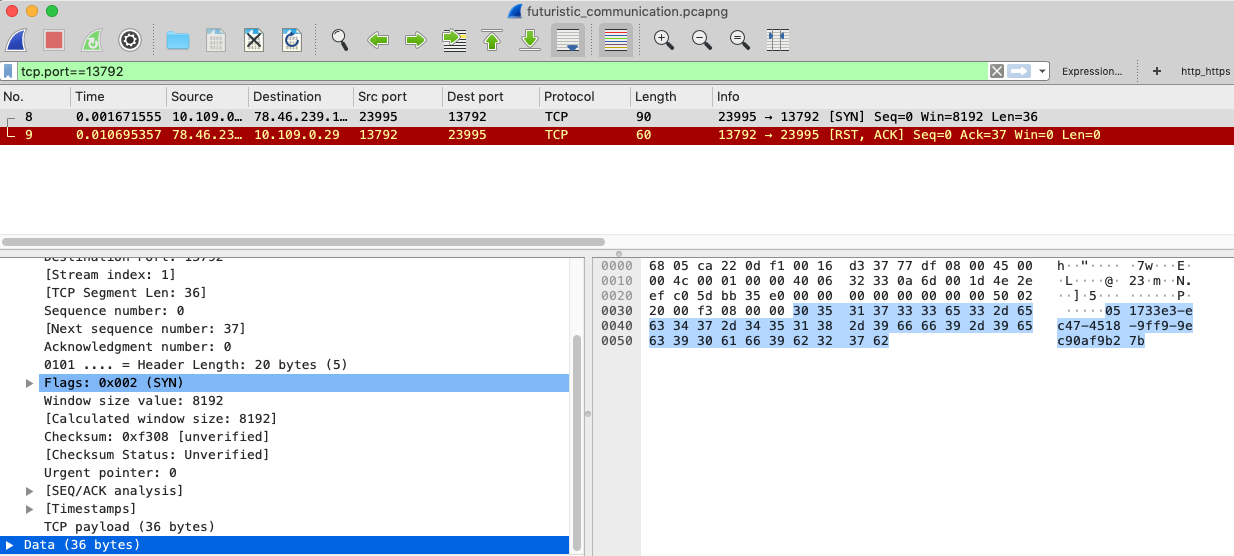
“tcp.port==38462” でフィルターすると、受け取った sequence number をSYNパケットにくっつけて送っているのが見えます。あと、personal identifier も付いてます。
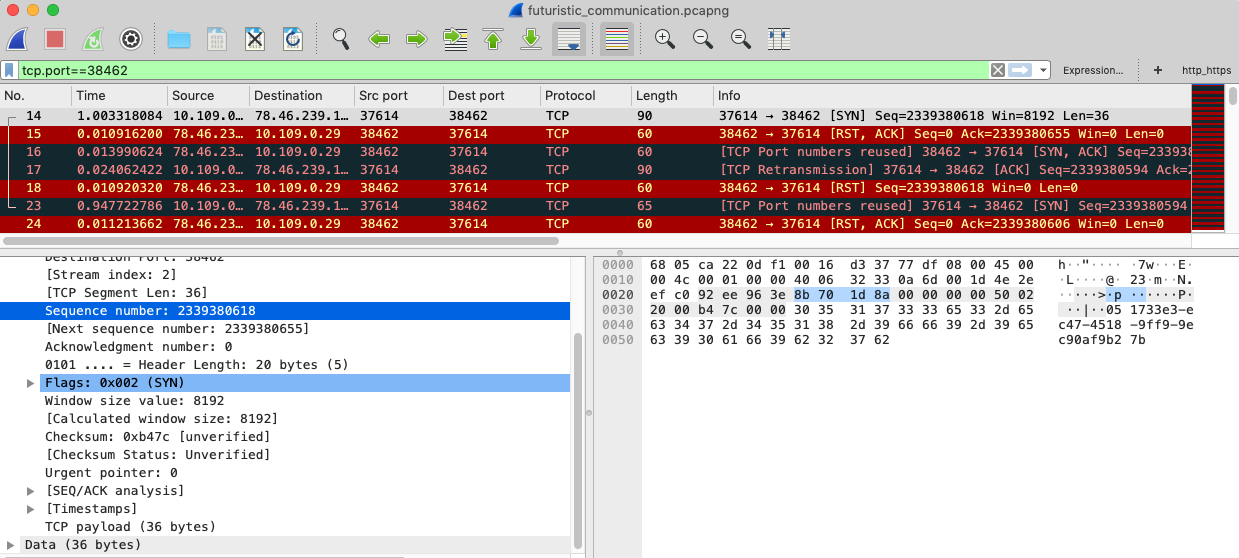
これを見る限り、SYNを送った後にまずRSTが返り、その後SYN/ACKが返ってくるように見えます。
とりあえず、ここまでの処理をScapyを使って書きました。
|
|
残念ながら、sequence numberを指定した SYNパケットがInvalidのようです。
以下、Follow TCP Streamです。
Welcome to handshake in future! Your personal identifier is: ae08b500-d644-47fa-9c7e-23acbd82d00f Waiting for identification, on TCP port 20428 Identification successful. Waiting for further instructions. Expecting handshake, on TCP port 54538, with sequence number 728714096 Invalid packet. Exiting <==これ
“tcp.port==54538” でフィルターしたものです。sequence number もちゃんと設定できているし、合っていると思うんですけどね。どこら辺がInvalidなのかわかんないです。
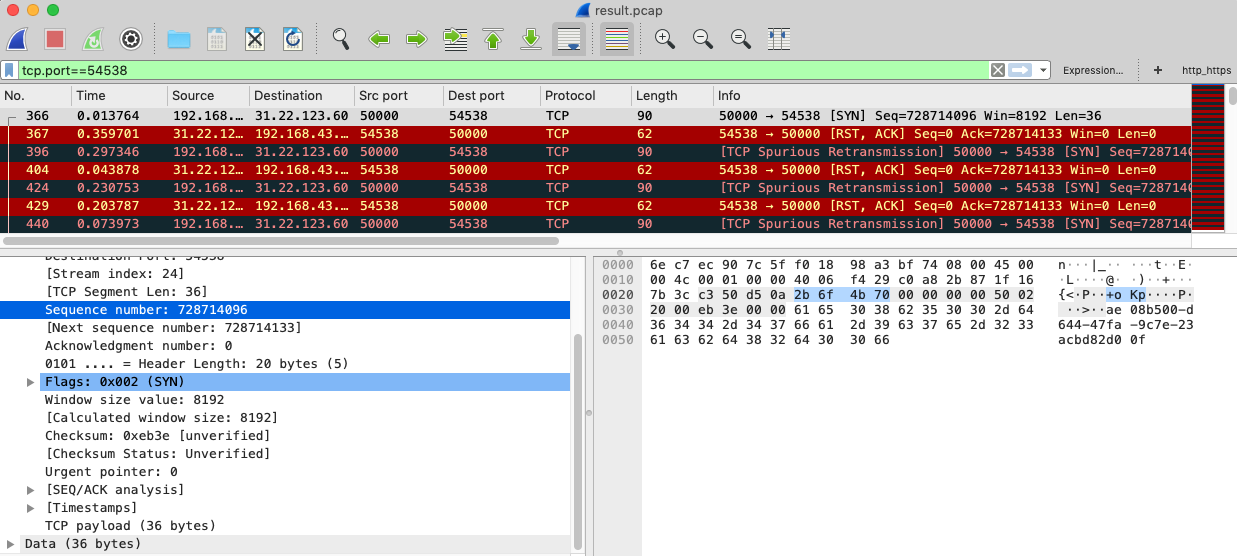
Handshakeがうまく行けば、あとは、synchronize、privileged、flagコマンドを送るだけなんだと思います。
|
|
なお、SYN/ACKを受信するにあたって、iptablesの設定も要ります。今回は、SYNがInvalid packet扱いされているので、そこまで行ってないですけど。
Mac OSだと、pfctlでやるみたいです。
Author CaptureAmerica @ CTF フラxxグゲット
LastMod 2019-10-26
