BCACTF 5.0 Writeup
Contents


URL: https://bcactf.com/
BCACTF は、4回目の参加です。去年(2024年)は何故か参加しなかったみたいです。たぶん、モンハンにハマってた時期だと思います。
BCACTF 1.0 (62位)
BCACTF 2.0 (63位)
BCACTF 3.0 (54位)
BCACTF 4.0 - 不参加
今回は610点を獲得し、最終順位は239位でした。だいぶチャレンジの難易度が上がってきていますね。

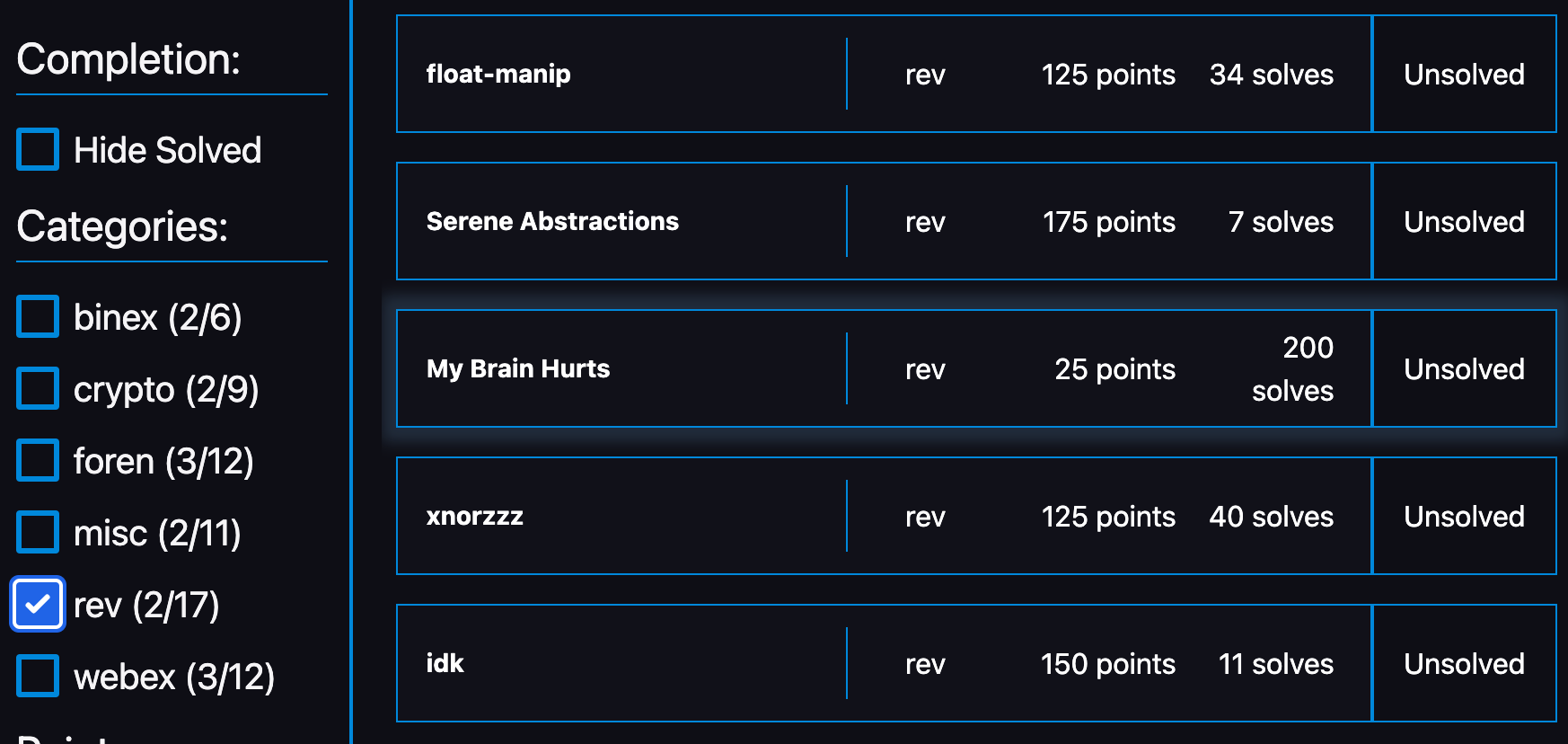
以下はチャレンジのリストです。
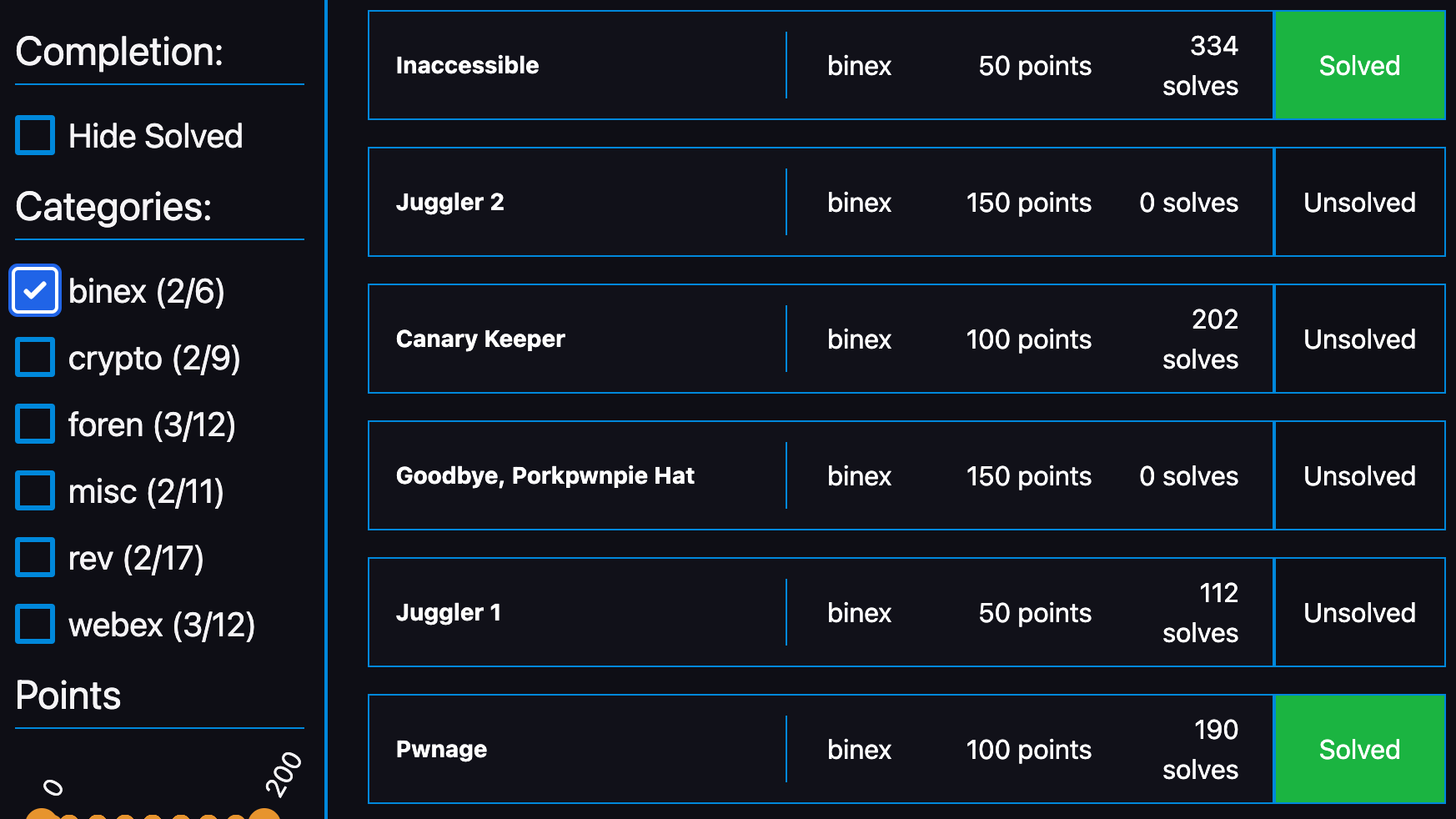
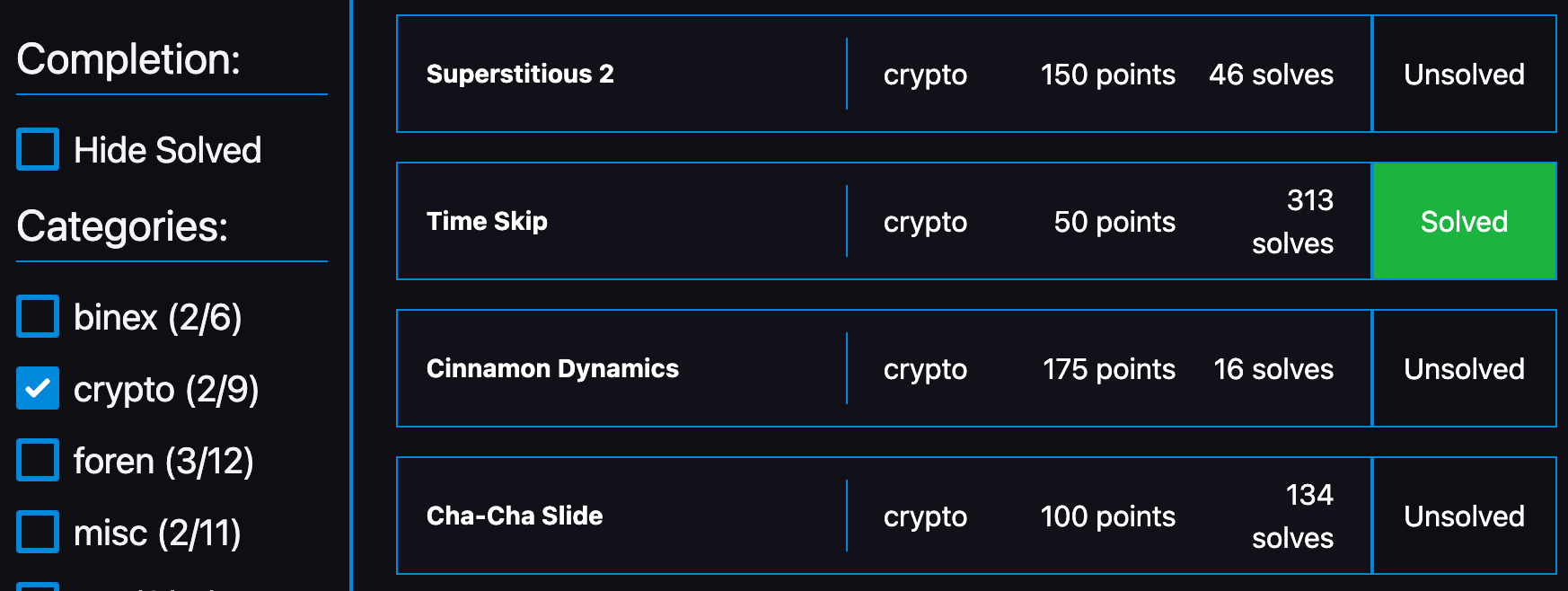
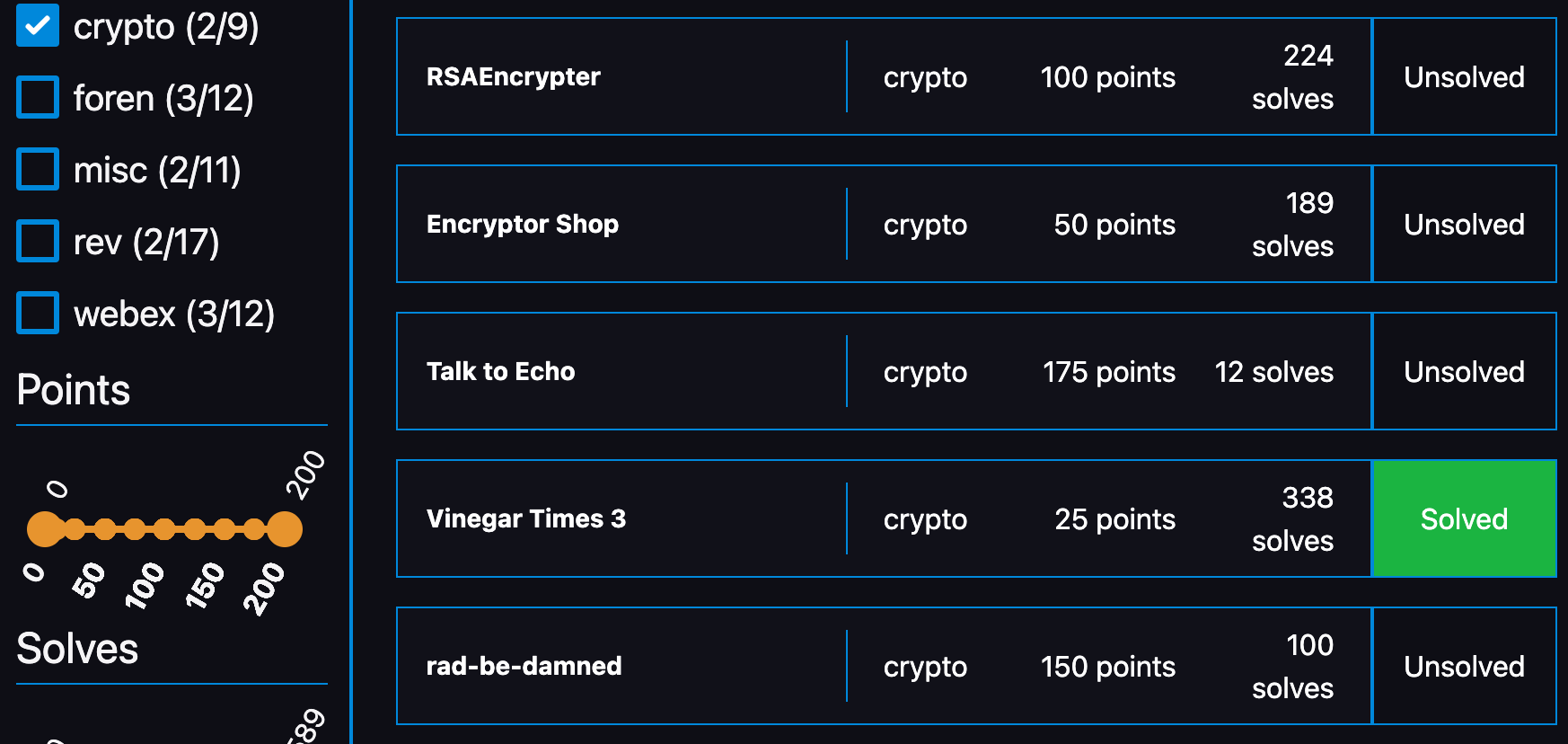
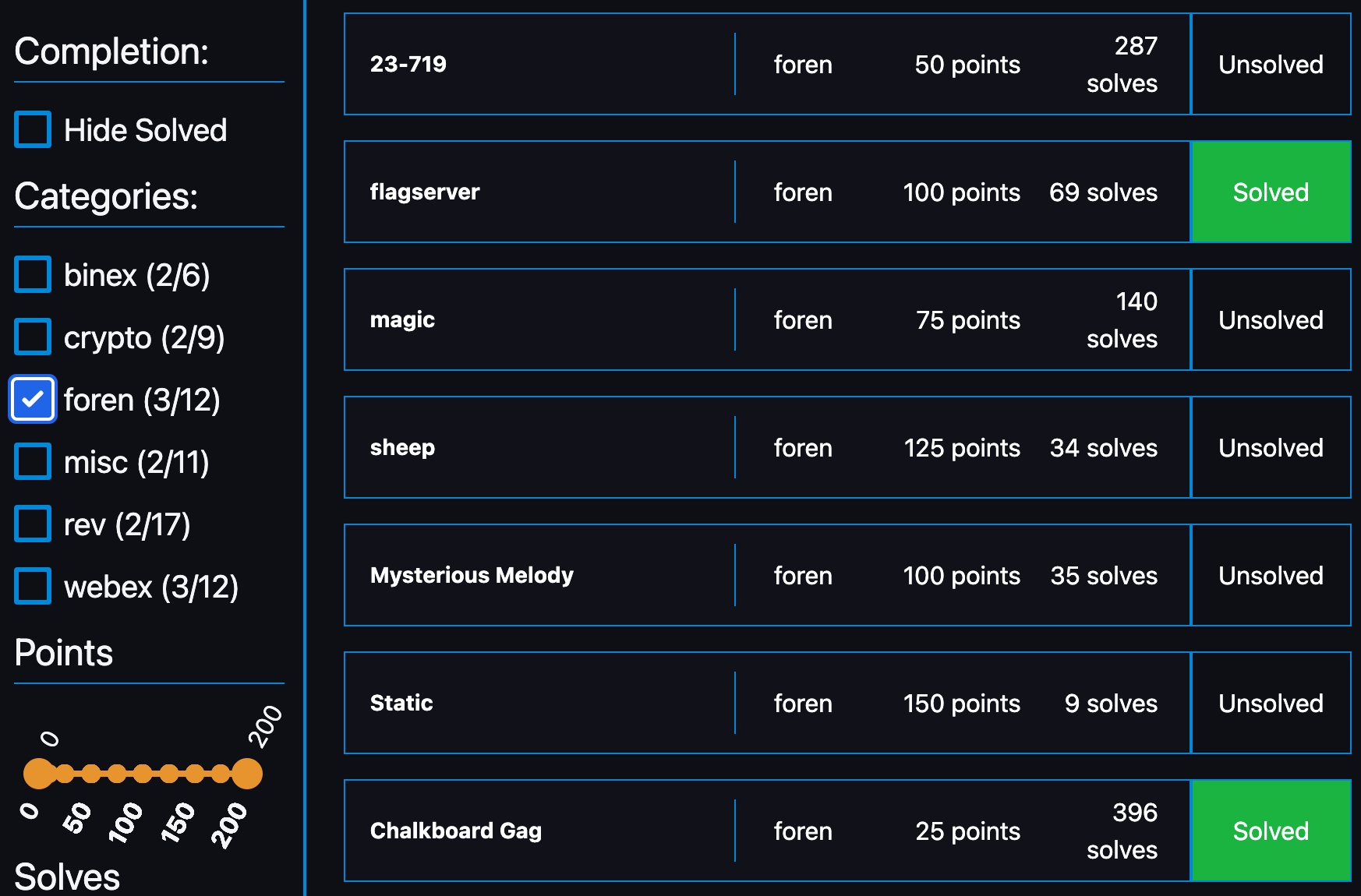
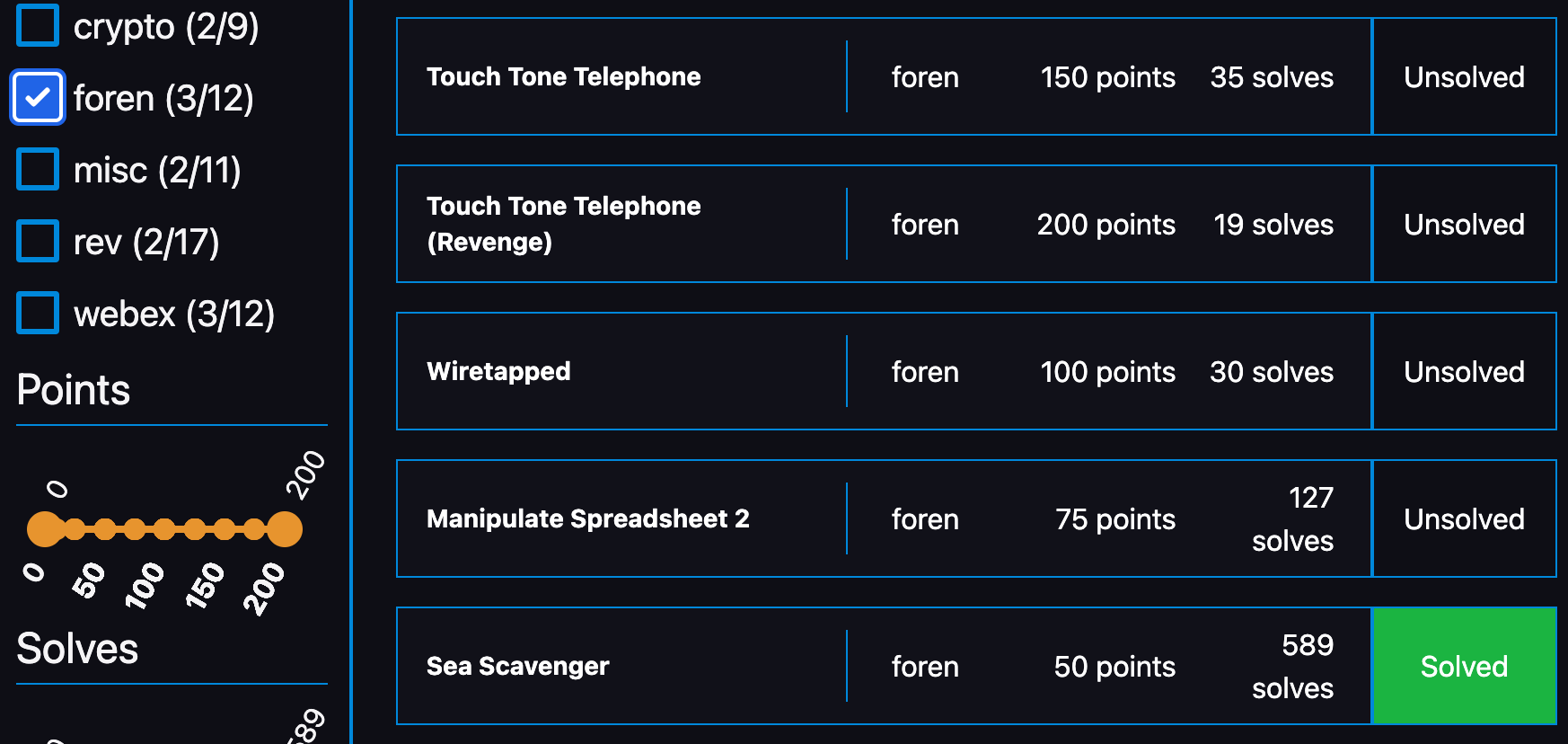
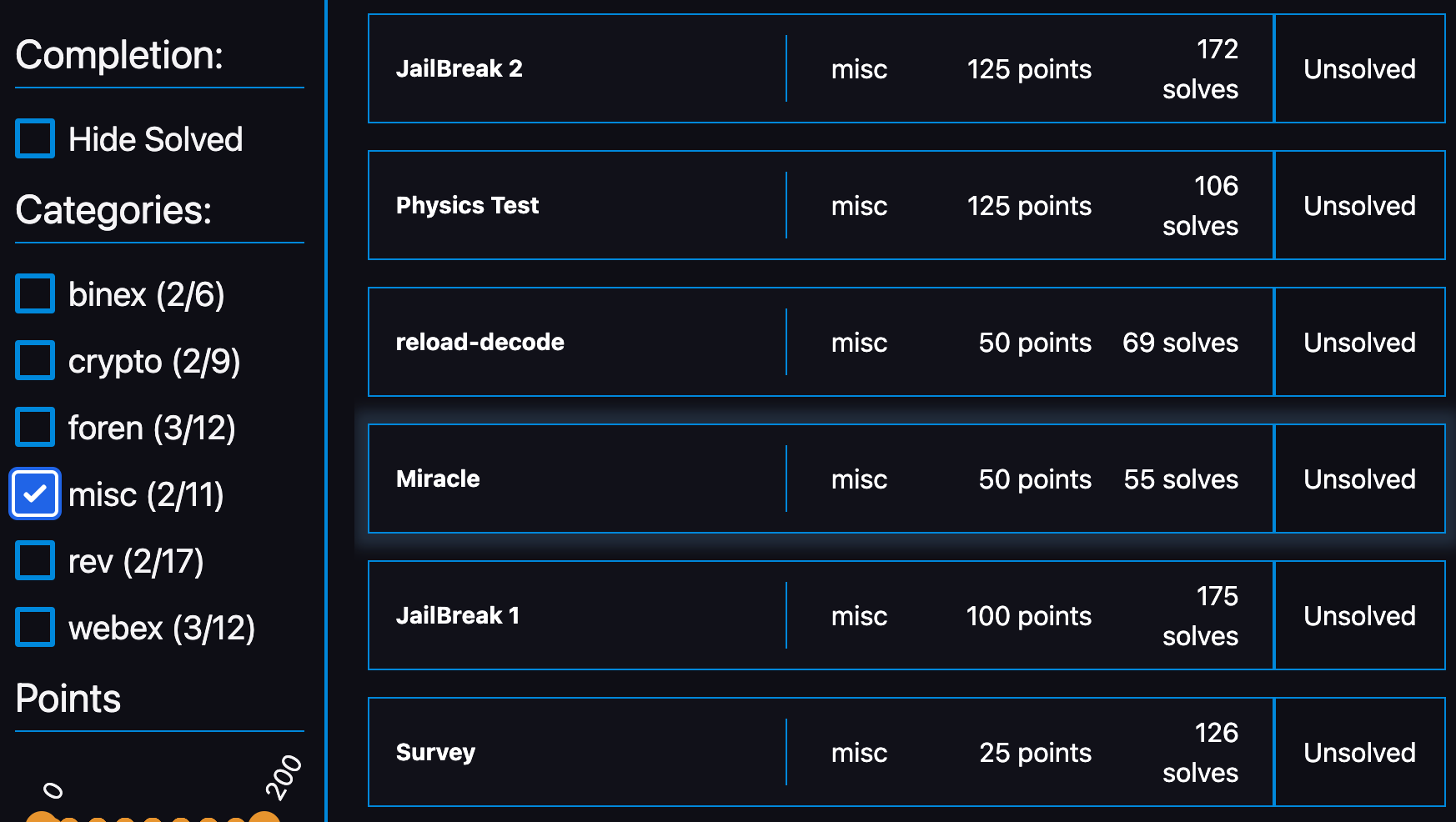
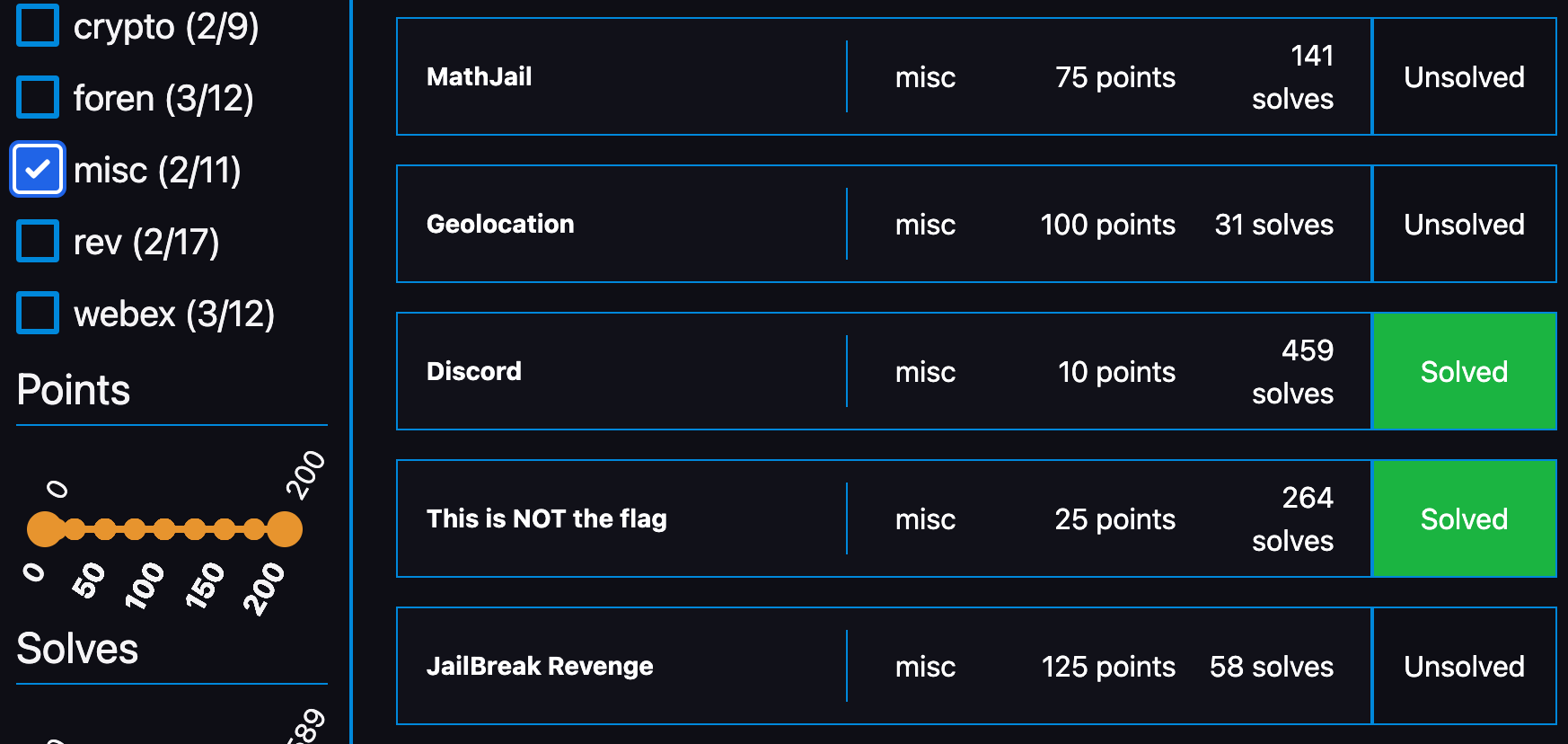
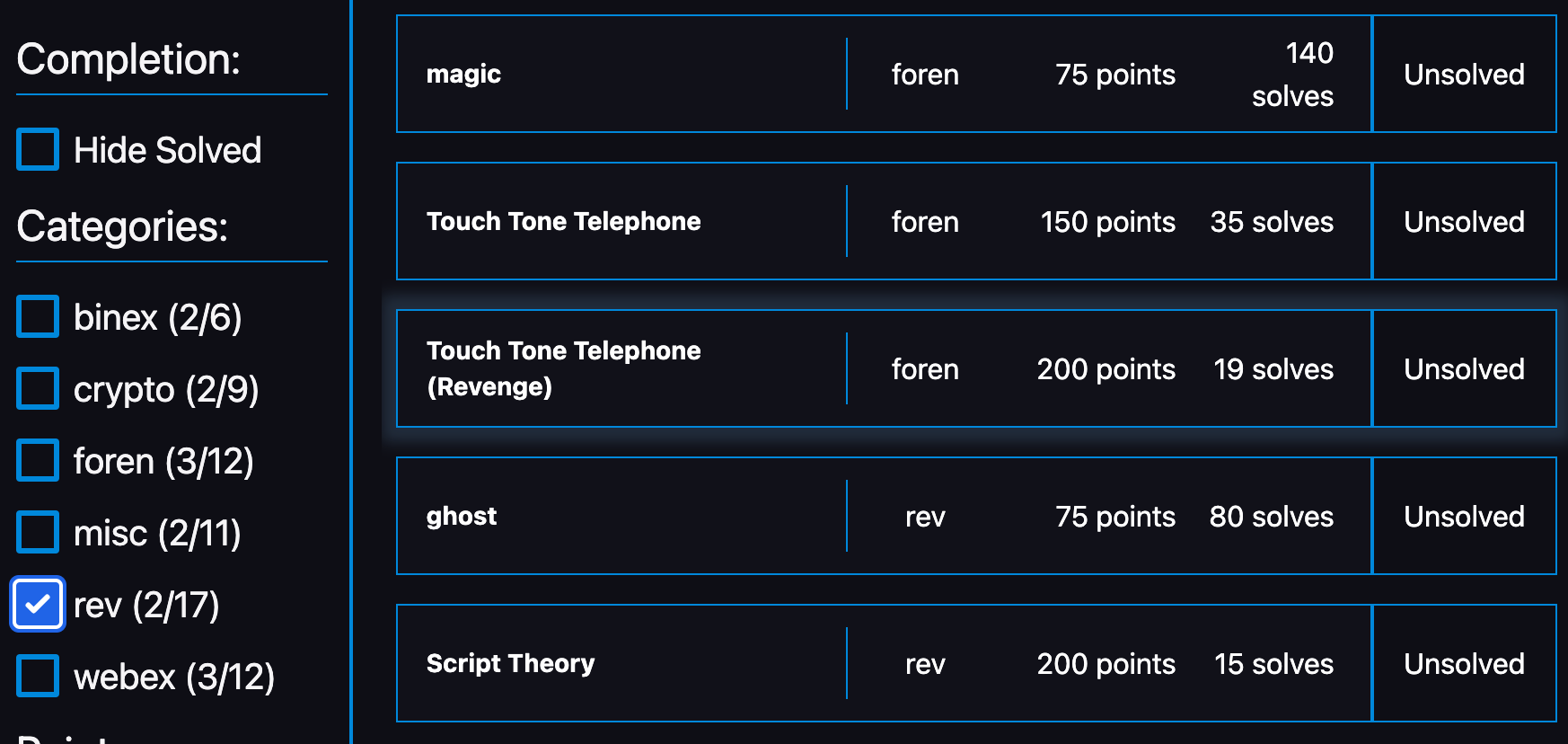
[Foren]: flagserver (100 points)
Challenge
It looks like Ircus have been using a fully exposed application to access their flags! Look at this traffic I captured. I can’t seem to get it to work, though… can you help me get the flag for this very challenge?
nc challs.bcactf.com 30145
Attachment:
- flagserver.pcapng
Solution
基本的には、Wiresharkで flagserver.pcapng を開いて、payload をバイナリファイルとして保存し(Export Packet Bytes)リプレイするだけです。
以下のpayloadは、バイナリエディタで編集が必要です。
BCACTF_2024 $ xxd 3_org.bin 00000000: 7870 7400 0966 616b 6563 6861 6c6c xpt..fakechall
まず、fakechall を flagserver にしないといけないです。
その後、実際にやってみるとわかるのですが、flagserve のように9文字しか送信されないので、長さのパラメータが存在していることがわかります。“0x09” を “0x0A” に変更します。
BCACTF_2024 $ xxd 3.bin 00000000: 7870 7400 0a66 6c61 6773 6572 7665 72 xpt..flagserver
以下が書いたコードです。
|
|
コードの最後でフラグを表示しようとしましたが、結局、Wiresharkでトラフィックをキャプチャーしてフラグを確認しました。
Flag: bcactf{thankS_5OCK3ts_and_tHreADInG_clA5s_2f6fb44c998fd8}
[Foren]: Chalkboard Gag (25 points)
Challenge
Matt Groening sent me an unused chalkboard gag, he says there’s something special inside of it.
Attachment:
- chalkboardgag.txt
以下のようなファイル。
I WILL NOT BE SNEAKY I WILL NOT BE SNEAKY : (snip)
Solution
こんな感じのファイルです。ほとんどの行は、I WILL NOT BE SNEAKY ですが、そうでない行がいくつかあります。
$ cat chalkboardgag.txt | sort | uniq -c
1 I WI1L NOT BE SNEAKY
1 I WIDL NOT BE SNEAKY
2 I WILL N0T BE SNEAKY
1 I WILL NOT B3 SNEAKY
1 I WILL NOT BE SBEAKY
1 I WILL NOT BE SNEADY
99974 I WILL NOT BE SNEAKY
1 I WILL NOT BE SNEAKa
1 I WILL NOT BE SNEAKt
1 I WILL NOT BE SNEAK}
1 I WILL NOT BE SNEBKY
1 I WILL NOT BE SNEPKY
1 I WILL NOT BE SNEUKY
1 I WILL NOT BE SNRAKY
1 I WILL NOT BE SNuAKY
1 I WILL NOT Bf SNEAKY
1 I WILL NOT _E SNEAKY
1 I WILL NOT bE SNEAKY
1 I WILL NaT BE SNEAKY
1 I WILR NOT BE SNEAKY
1 I WILT NOT BE SNEAKY
1 I WILW NOT BE SNEAKY
1 I WIcL NOT BE SNEAKY
1 I W_LL NOT BE SNEAKY
1 I WcLL NOT BE SNEAKY
1 I _ILL NOT BE SNEAKY
1 I {ILL NOT BE SNEAKY
ということで、I WILL NOT BE SNEAKY 以外の行だけ取り出します。
$ grep -v "I WILL NOT BE SNEAKY" chalkboardgag.txt
I WILL NOT bE SNEAKY
I WIcL NOT BE SNEAKY
I WILL NOT BE SNEAKa
I WcLL NOT BE SNEAKY
I WILL NOT BE SNEAKt
I WILL NOT Bf SNEAKY
I {ILL NOT BE SNEAKY
I WILL NOT BE SNEBKY
I WILL NaT BE SNEAKY
I WILL NOT BE SNRAKY
I WILT NOT BE SNEAKY
I WILL NOT _E SNEAKY
I WILW NOT BE SNEAKY
I WILL N0T BE SNEAKY
I WILL NOT BE SNEUKY
I WI1L NOT BE SNEAKY
I WILL NOT BE SNEADY
I W_LL NOT BE SNEAKY
I WILL NOT BE SBEAKY
I WILL NOT B3 SNEAKY
I _ILL NOT BE SNEAKY
I WILL NOT BE SNEPKY
I WILR NOT BE SNEAKY
I WILL N0T BE SNEAKY
I WILL NOT BE SNuAKY
I WIDL NOT BE SNEAKY
I WILL NOT BE SNEAK}
コマンドを使ってもできたかもですが、ここからは手動でやりました。各行から変更されている文字を取り出すだけです。
Flag: bcactf{BaRT_W0U1D_B3_PR0uD}
[Binex]: Inaccessible (50 points)
Challenge
I wrote a function to generate the flag, but don’t worry, I bet you can’t access it!
Hint1: you could reverse engineer the function, but it’s not necessary
see if you can use any debugging tools to just call the function
Attachment:
- chall (ELF 64-bit)
Solution
ghidraでデコンパイルします。
|
|
フラグを表示するwin()関数が用意されていてますが、win()関数自体がどこからも呼ばれていない、というコードです。
gdbでwin()へjumpするだけです。
gef➤ b main
gef➤ r
gef➤ jump win
Continuing at 0x4005ee.
bcactf{W0w_Y0u_m4d3_iT_b810c453a9ac9}
Flag: bcactf{W0w_Y0u_m4d3_iT_b810c453a9ac9}
[Binex]: Pwnage (100 points)
Challenge
It’s either a bug, a hack, an exploit, or it’s pwnage.
Let this challenge stand as one of the first of many stairs to mastery over that which can only be described as pwn.
nc challs.bcactf.com 31049
Attachment:
- provided.c
中身:
|
|
Solution
とりあえず、ncで繋いで動作を見てみます。
$ nc challs.bcactf.com 30810 Welcome to the most tasmastic game of all time! . . . Basically it's just too simple, I've put the flag into the memory and your job is ... to guess where it is!! . . How fun is that! . Oh and before you start, I'll give you a little hint, the address of the current stackframe I'm in is 0x7ffe71e7eaf0 . . . Okay anyway, back to the game. Make your guess! (hexadecimals only, so something like 0xA would work) guess>
first_var のポインターが表示されます。その後、任意のポインターを入力すると、その部分のデータを表示してくれるプログラムなのがわかります。
flagのポインターは、first_var のポインター + 32 bytes です。
32 bytesがわからなくても、トライアンドエラーでも解くことができると思います。
>>> hex(0x7ffe71e7eaf0 + 32) '0x7ffe71e7eb10'
guess> 0x7ffe71e7eb10
. . .
Okay, prepare yourself. If you're right this
will print out the flag
.
Oh, and if your wrong, this might crash and
disconnect you
Good luck!
bcactf{0nE_two_thR3E_f0ur_567___sT3ps_t0_PwN4G3_70cc0e5edd6ea}
Flag: bcactf{0nE_two_thR3E_f0ur_567___sT3ps_t0_PwN4G3_70cc0e5edd6ea}
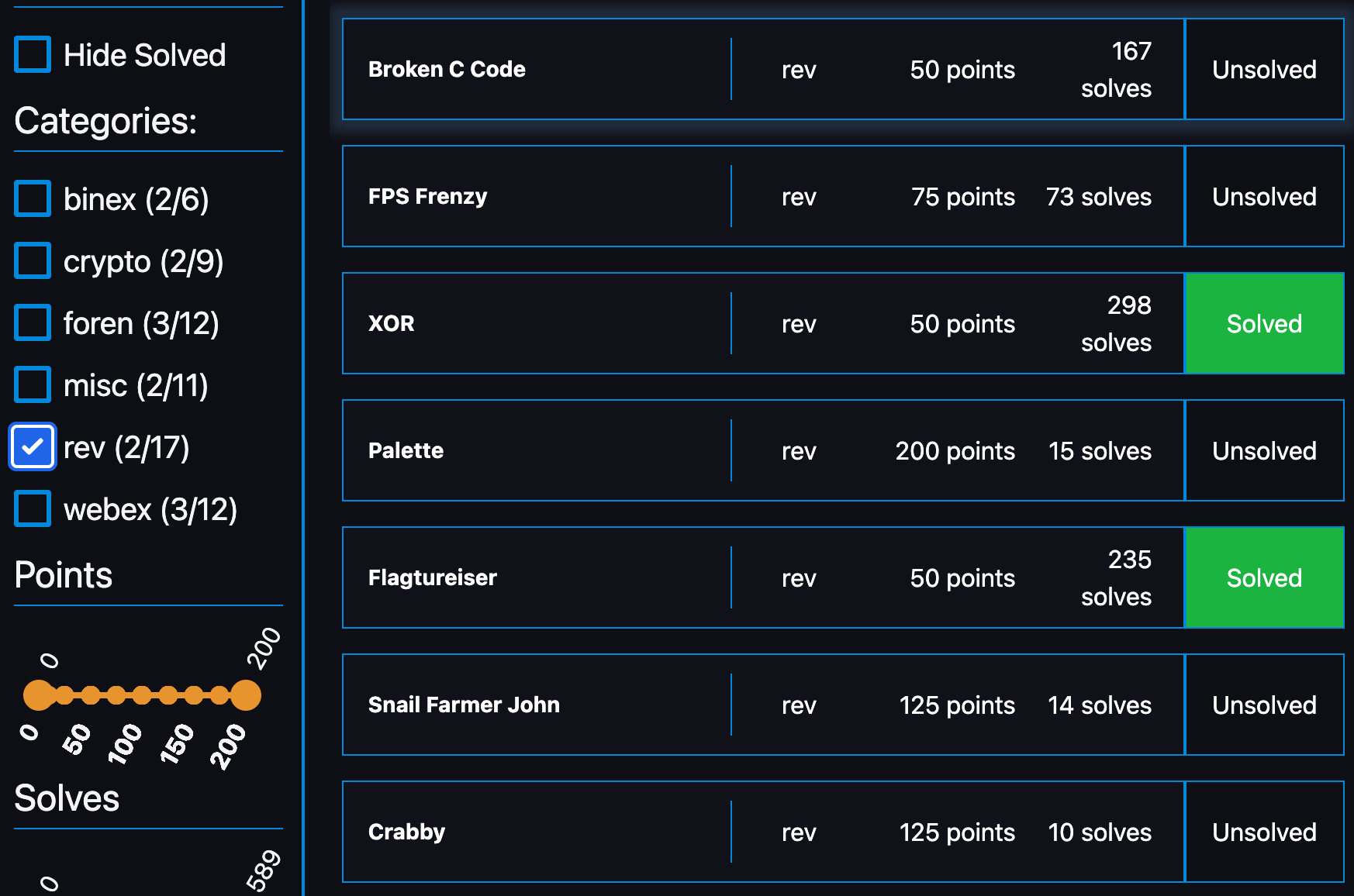
[Rev]: XOR (50 points)
Challenge
The executable below outputs an encrypted flag using the XOR operator. Can you decompile and reveal the flag?
nc challs.bcactf.com 32411
Attachment:
- xor (ELF 64-bit)
Solution
ghidraでデコンパイルします。
|
|
ncで繋いで、動作も見てみます。
$ nc challs.bcactf.com 32411 Encrypted flag: 21 0F 0A 15 3F 29 29 6B 13 1C 2C 74 7D 30 5E 50 6E 29 2B 24 19 0C 67 7D 05 54 7C 34 5C 13 32 42 29 62 7B 0F 4E
ClkvKOR8JQA1JB731LeGkU7J4d2khDvrOPI63mM7 をKeyとしてXORするだけです。CyberChefを使いました。
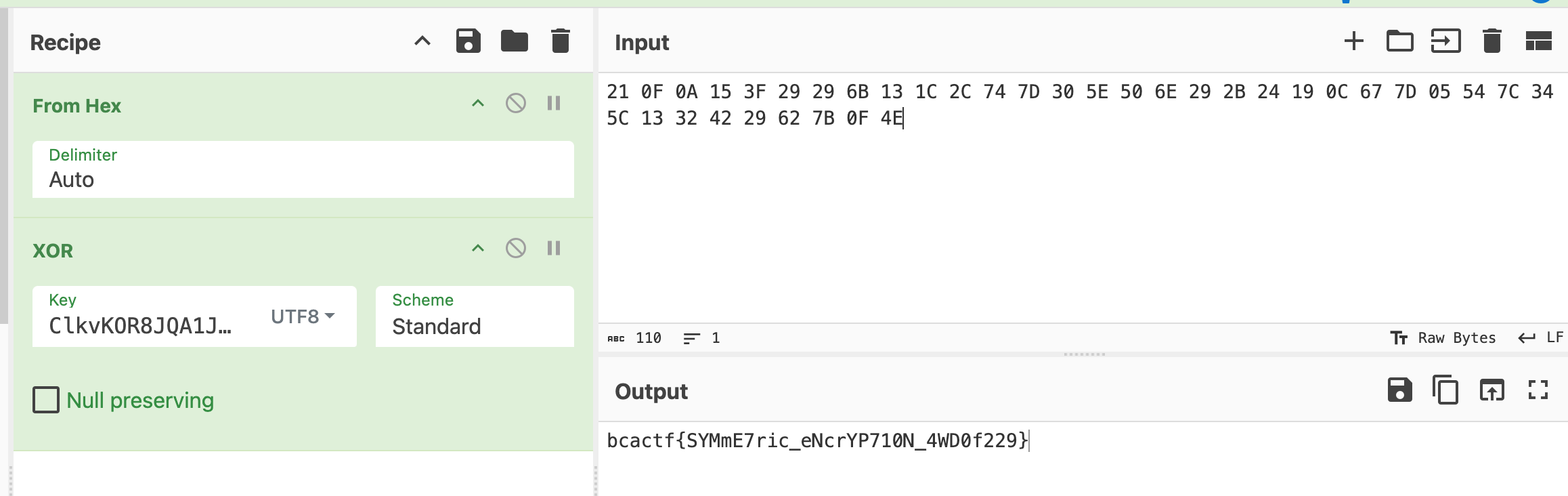
Flag: bcactf{SYMmE7ric_eNcrYP710N_4WD0f229}
[Rev]: Flagtureiser (50 points)
Challenge
Here’s a totally normal Minecraft mod (1.19.4, Forge) I’ve been making, check it out!
(You do not need Minecraft to solve this challenge)
Attachment:
- flagtureiser-4.2.0.6.9.jar
Solution
Jarファイルを JD-GUI で開いて、見つけた数字を CyberChef で文字にするだけです。
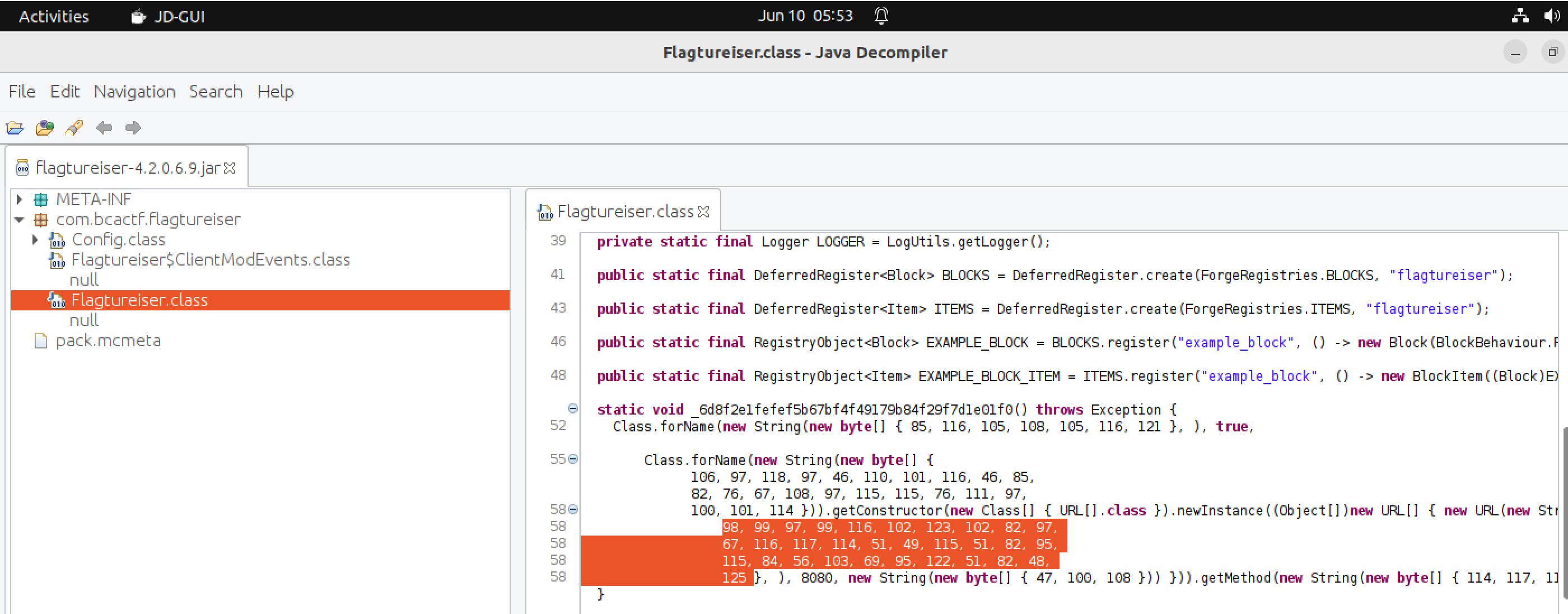
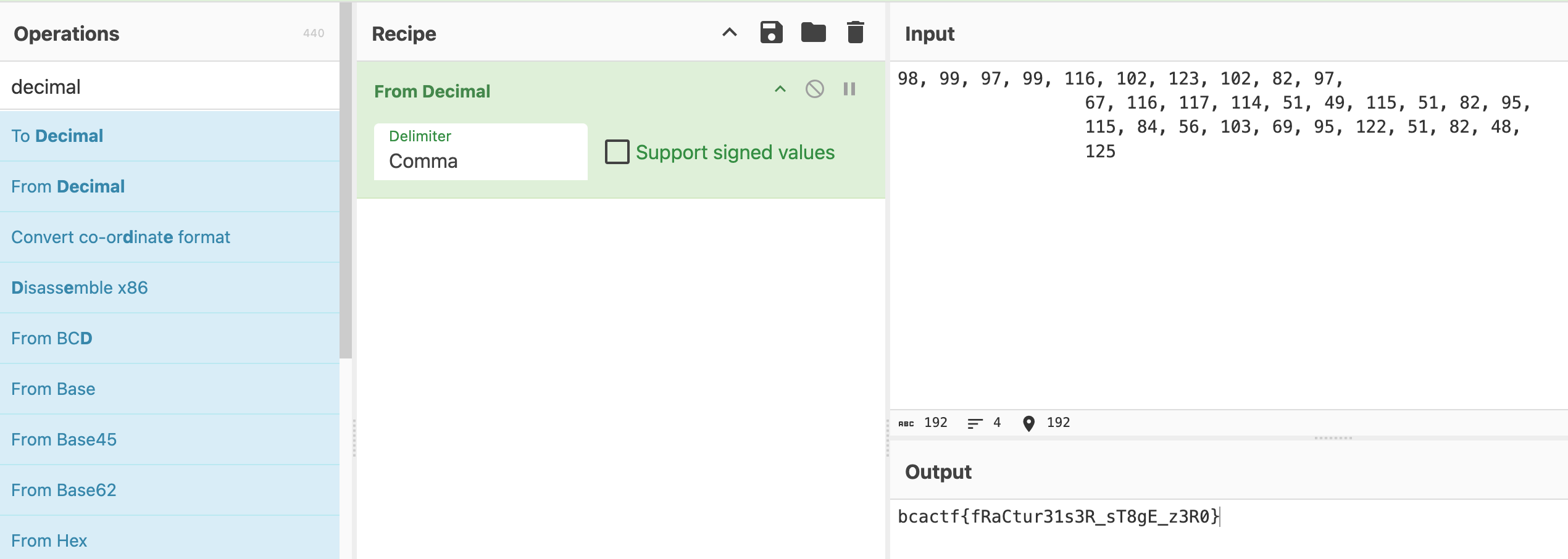
Flag: bcactf{fRaCtur31s3R_sT8gE_z3R0}
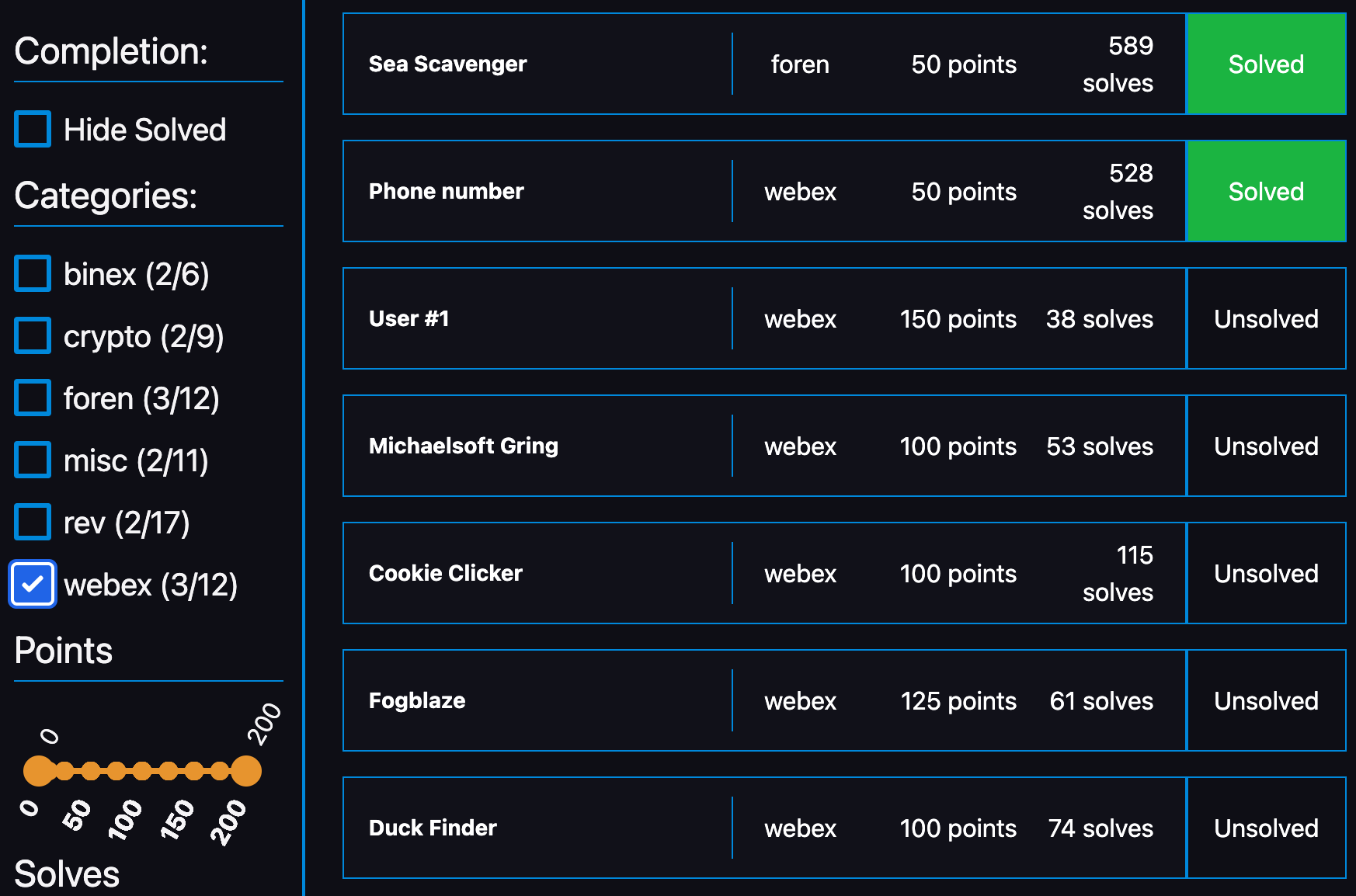
[Web]: NoSQL (25 points)
Challenge
I found this database that does not use SQL, is there any way to break it?
challs.bcactf.com:30390
Hint: Ricardo Olsen has an ID of 1
Attachment:
- provided.js
中身:
|
|
Solution
与えられたヒント Ricardo Olsen has an ID of 1 とコードを見ると、以下にアクセスしたら何か得られるはずだと思ったんですが、Not Valid Queryというエラーが出るだけだったので小一時間悩みました。
http://challs.bcactf.com:30390/1/Ricardo/Olsen
21行目のところで正規表現を使って line.match() をしているので、.* を入れたらテーブルの中身が全部取れました。
http://challs.bcactf.com:30390/?name=.*
{"rtnValues":["Ricardo Olsen","April Park","Francis Jackson","Ana Barry","Clifford Craig","Andrew Wise","Ada Atkinson","Janis McIntosh","Rosie Parsons","Neal Weaver","Alyssa Robison","Michael Hurst","Roberto Thornton","Renee Schwartz","Darryl Wilson","Wayne Boyle","Loretta Camacho","Bert Morton","Suzanne Johnson","Carol Fowler","Rose Hansen","Aimee Norman","Bethany Foley","Benjamin Baily","David Hull","Sabrina Fish","Rick Kirby","Edgar Grimes","Blake McDermott","Alicia Crosby","Teresa Ortega","Carroll Darling","Louis Tate","Phillip Fuller","Clinton Kimball","Alma Matthews","Stacie Franklin","Lucinda Steward","Gina Andrews","Philip Hyde","Devin Riggs","Michelle Thornton","Rogelio Freeman","Arthur Stephens","Andy Leon","Megan Gould","Myrna Yates","Edwin Pearce","Shirley Cannon","Lowell Cochran","Flag Holder"]}
末尾の51番目の要素のところに、それっぽいユーザ(Flag Holder)がいます。
ということで、以下でフラグが取れます。
http://challs.bcactf.com:30390/51/Flag/Holder
Flag: bcactf{R3gex_WH1z_54dfa9cdba13}
[Crypto]: Time Skip (50 points)
Challenge
One of our problem writers got sent back in time! We found a piece a very very old piece of parchment where he disappeared, alongside a long cylinder. See if you can uncover his flag!
Attachment:
- parchment.txt
中身:
hsggna0stiaeaetteyc4ehvdatyporwtyseefregrstaf_etposruouoy{qnirroiybrbs5edmothssavetc8hebhwuibihh72eyaoepmlvoet9lobulpkyenf4xpulsloinmelllisyassnousa31mebneedtctg_}eeedeboghbihpatesyyfolus1lnhnooeliotb5ebidfueonnactayseyl
Solution
“parchment cylinder cipher” を Keyword としてググって、Scytale Cipher を見つけました。
https://www.dcode.fr/cipher-identifier を使っても、4番目の候補として出てくるので、一個一個試したら解けますね。
Decryptした中にフラグが出てきます。
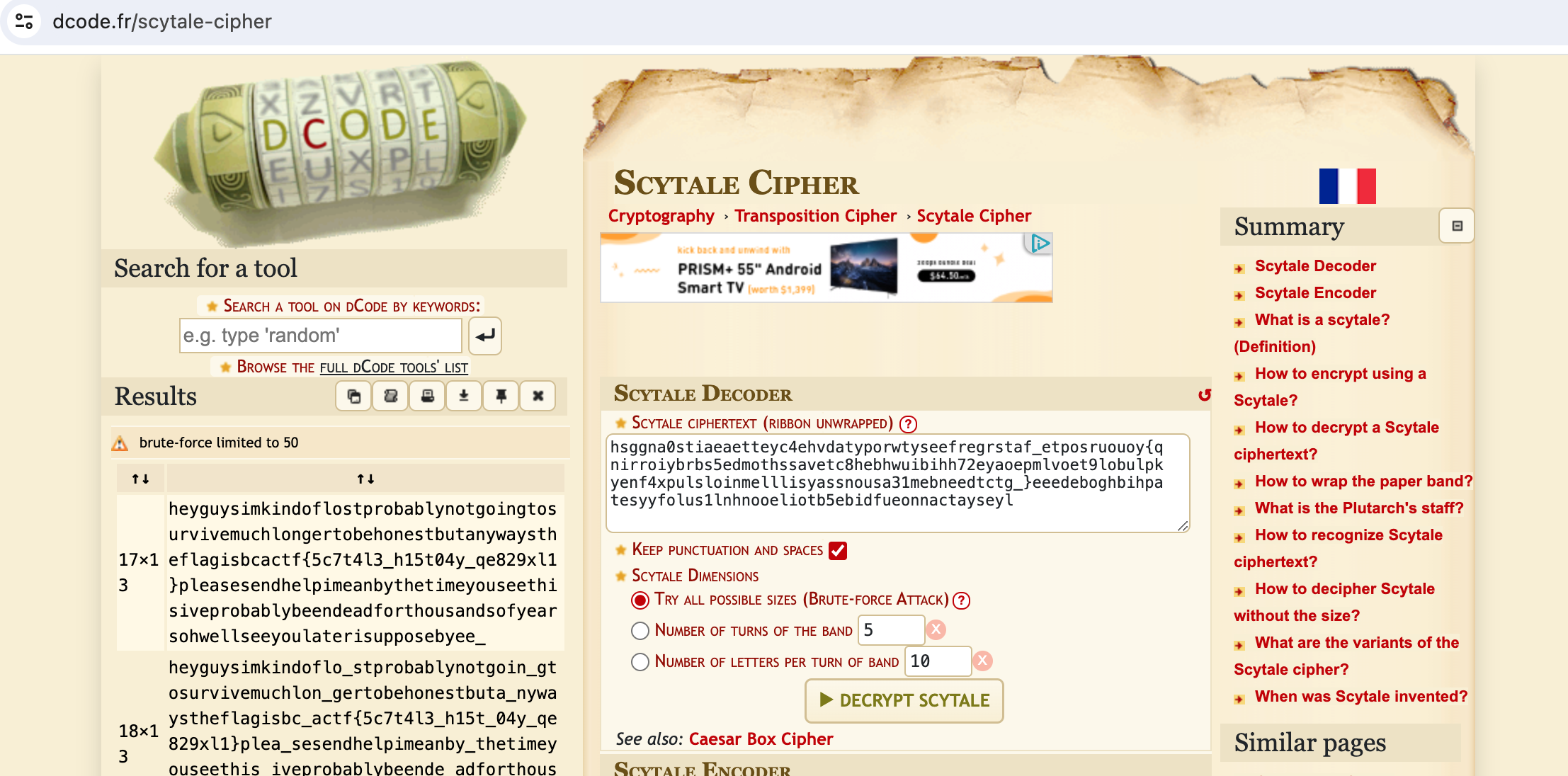
Flag: bcactf{5c7t4l3_h15t04y_qe829xl1}
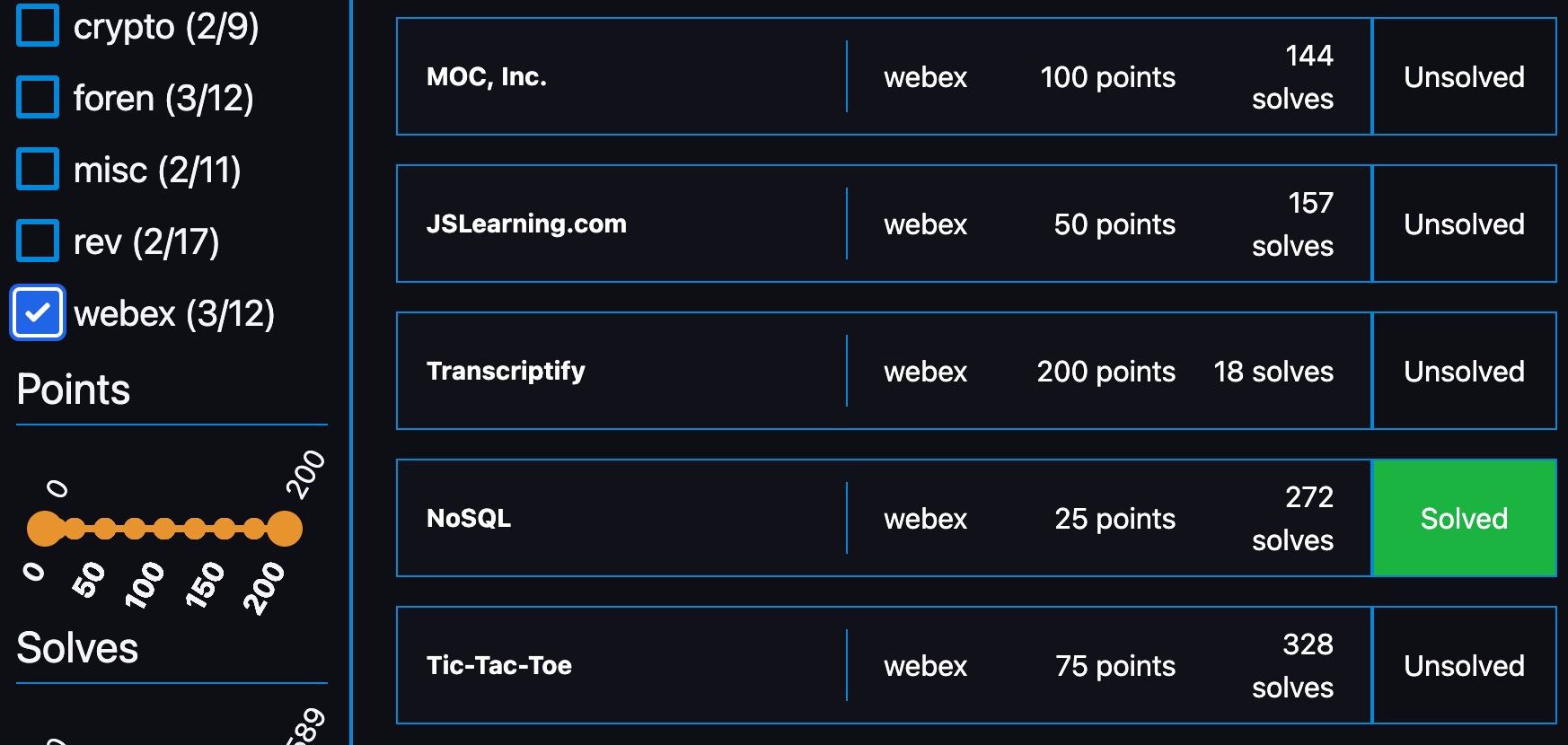
[Foren]: magic (75 points)
Challenge
I found this piece of paper on the floor. I was going to throw it away, but it somehow screamed at me while I was holding it?!
Attachment:
- magic.pdf
(Unsolved)
Javascriptの難読化が解けなくて、降参しました。
$ python3 ./pdf-parser.py -o 2 -f -d obj.bin magic.pdf
obj 2 0
Type: /ObjStm
Referencing:
Contains stream
<<
/Type /ObjStm
/N 30
/First 224
/Length 2622
/Filter /FlateDecode
>>
$ strings obj.bin | grep -i flag
:
(snip)
:
以下は、Beautifyした後のコードです。少し編集もしています。
|
|
node コマンドを使って実行してみたりしたけど、よくわからなかったです。。。
Author CaptureAmerica @ CTF フラxxグゲット
LastMod 2024-06-12
