DeconstruCT.F 2021 Writeup
Contents


URL: https://ctf.dscvit.com/challenges
1450点を獲得し、79位でした。

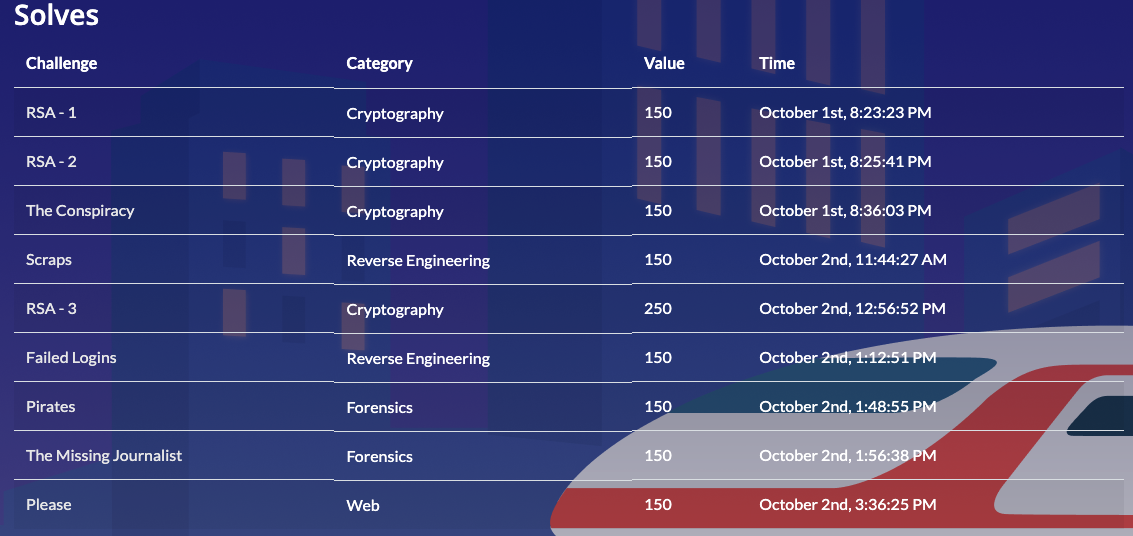
チャレンジのリストです。

[Crypto]: RSA - 3 (250 points)
Challenge
Alright, this is the big leagues. You have someone’s Public Key. This isn’t unusual, if you want to send someone an encrypted message, you have to have thier public key. Your job is to evaluate this public key, and obtain the value of the secret exponent or decryption exponent (The value of “d” in an RSA encryption).
Wrap the number that you find with dsc{}!
Attachment:
- mykey.pub
Solution
まず、以下を試したのですが、エラーになりました。
$ ssh-keygen -f mykey.pub -e -m pem | openssl asn1parse Load key "mykey.pub": invalid format Error: offset out of range
そこで、RsaCtfTool.py を使って private key を出力しました。
$ ~/Python3/RsaCtfTool/RsaCtfTool.py --publickey ./mykey.pub --private
-----BEGIN RSA PRIVATE KEY-----
MIIEXwIBAAKCAQEB+34C7GuhHbhLHus9oqCfHR5N2e6WlnXb+MP5qCbY9fbjoWmg
VqKTRu8Zv81KjjlQ531oc8x4tf0H4kyuPjngAI0UjWdEcNnNWy7ErnJzdwW8jGrZ
Spj7BZe9eoPdo3l16lnTDQCxTnm/1YF+crA1Ek7wIQG5S0fguTGebiwLX79qVFcC
RvCccSQKhiuJiZjK0MOrWYlnm8O518tw0ZUuaFhgtFaBJyTI04aN5oTZF3gyuPDZ
8MCTp7wYoJ4CvcONlUpobAqSZ1/VIqDxlYM2Yo6h101wGzW/jucsg+8Np+V+4vHX
aSLpz6DOhA7TZIAozzL+4I5SfL0lzzfXSQB8CQKCAQEBHvBcAbNv9v7I/ZieaKjZ
xEclI5AXjA/igQcW4sz7uHPyt0/5aX5TGEkrfROs9renIw7JTkXeo9uArubEIcp4
7g4346dg5i0tmxbUzF/Pzz3JJGqygmhbVnIlMP93Iwm2VUOMuTSffK01NdmyysC7
xy0OudHb+GtzUv40H2rcTe6VqPuV0pVY5qivnjPeBKl5TVsxrwbyVXdj+1hjh2pw
c2fUZY1LZUAhybrxK/9d2LcZeidUK8IWV92zgE/AYbNDsbwruLR91iO9DTEH99z0
OIjMj/xnIkY/kb8j5lCdIITsU8VxAdzkx05IIa54t6o2+2vXKYfQgSwjeXRBywgg
lQJAehHdzEMx5okjFvPpElQjZWvTuYT9AG04F4b2MMWiMLeLPIt8Clma+tHt2G/A
BWuujnW/UDFVxGsk6KhvsIfWFQKBgQEJOVoWZwRXdfRDN0Ws3dF7NI5Ju9P65hyt
ByBC3WlEZH9R2utRURFIRfaxVmAedseDfUrurqFdWLSYGT2yawBoYQq2uDRVB6P7
5RiVZIhKJjeZllIlKAUwPqbcTpeyxsL9izDxZrq14PzvUjjpa9lpCD4jbEHGhiap
oQqApHMDVwKBgQHp17BSkIX1r+qAPtsBuOMeQIONQx5+8cl8CKpW9bOSWq3vWTYE
La8xGU7ri9Sg4p2pkHV3mZwIdSeGj7iOgLUykYoDzKWxwqxU5K9hYr7Jl64TLwJG
N8JKBRFvcWr1RTu6K9HV3jMqj7r/Y14QMYZevn+7XUFJ5MqsmVnGNdk/nwJAehHd
zEMx5okjFvPpElQjZWvTuYT9AG04F4b2MMWiMLeLPIt8Clma+tHt2G/ABWuujnW/
UDFVxGsk6KhvsIfWFQJAehHdzEMx5okjFvPpElQjZWvTuYT9AG04F4b2MMWiMLeL
PIt8Clma+tHt2G/ABWuujnW/UDFVxGsk6KhvsIfWFQKBgQDOrWptQGDlH1VYjTk2
PvGX6PEiClix9zUvEicK6naC7cyz0LvNY0FtVY/uwhyv2sFxceH1LxdlsPy+xWFN
/GHaIoCU00C0Anq6eOqDKynvPlt4YYNI5EtFoi/r/dzioxHTXCiwbOeIkYWytmKF
6OXjzPgDat8h322YbtYnj8mfXg==
-----END RSA PRIVATE KEY-----
$ ssh-keygen -f mykey_private.key -e -m pem | openssl asn1parse
0:d=0 hl=4 l= 522 cons: SEQUENCE
4:d=1 hl=4 l= 257 prim: INTEGER :01FB7E02EC6BA11DB84B1EEB3DA2A09F1D1E4DD9EE969675DBF8C3F9A826D8F5F6E3A169A056A29346EF19BFCD4A8E3950E77D6873CC78B5FD07E24CAE3E39E0008D148D674470D9CD5B2EC4AE72737705BC8C6AD94A98FB0597BD7A83DDA37975EA59D30D00B14E79BFD5817E72B035124EF02101B94B47E0B9319E6E2C0B5FBF6A54570246F09C71240A862B898998CAD0C3AB5989679BC3B9D7CB70D1952E685860B456812724C8D3868DE684D9177832B8F0D9F0C093A7BC18A09E02BDC38D954A686C0A92675FD522A0F1958336628EA1D74D701B35BF8EE72C83EF0DA7E57EE2F1D76922E9CFA0CE840ED3648028CF32FEE08E527CBD25CF37D749007C09
265:d=1 hl=4 l= 257 prim: INTEGER :011EF05C01B36FF6FEC8FD989E68A8D9C447252390178C0FE2810716E2CCFBB873F2B74FF9697E5318492B7D13ACF6B7A7230EC94E45DEA3DB80AEE6C421CA78EE0E37E3A760E62D2D9B16D4CC5FCFCF3DC9246AB282685B56722530FF772309B655438CB9349F7CAD3535D9B2CAC0BBC72D0EB9D1DBF86B7352FE341F6ADC4DEE95A8FB95D29558E6A8AF9E33DE04A9794D5B31AF06F2557763FB5863876A707367D4658D4B654021C9BAF12BFF5DD8B7197A27542BC21657DDB3804FC061B343B1BC2BB8B47DD623BD0D3107F7DCF43888CC8FFC6722463F91BF23E6509D2084EC53C57101DCE4C74E4821AE78B7AA36FB6BD72987D0812C23797441CB082095
nとeを10進数になおして、以下のコードで d を求めました。
|
|
Flag: dsc{6393313697836242618414301946448995659516429576261871356767102021920538052481829568588047189447471873340140537810769433878383029164089236876209147584435733}
[Rev]: Failed Logins (150 points)
Challenge
Our supreme leader Rithicc was asked to store a flag, but he misunderstood and made an app instead (which he always does) smh
Attachment:
- chall.apk
Solution
実は、Android Studio使って実際に動かしたり、decompileしてコードを見たりして色々やったのですが、結局のところ、以下の方法でフラグは取れます。
.apkファイルは zip圧縮されたファイルなので、まずunzipします。
次に、出てきた classes.dex に対して strings をかけて、見つかった flag の元を rot13 するとフラグが得られます。
$ strings classes.dex | grep "flag"
, flags=
KCalled removeDetachedView with a view which is not flagged as tmp detached.
Must provide flag PRE or POST
+Only MODE_IN and MODE_OUT flags are allowed
Pattern.compile(pattern, flags)
Requested flags 0x
mStable Ids are required for the adapter to function properly, and the adapter takes care of setting the flag.
flag
%flag=qfp{4aqe01q_4cx_p4a_83_e3i3e53q}
Flag: dsc{4ndr01d_4pk_c4n_83_r3v3r53d}
[Rev]: Scraps (150 points)
Challenge
One of our coders have locked down an application that is scheduled to be released tommorow.
Can you unlock the application as soon as possible.
Attachment:
- Release-1.0 (ELF 64bit)
Solution
Ghidraでコードを確認します。
|
|
とりあえず、文字になりそうな箇所(ハイライト部分)があるので変換します。
反転して base64 デコードするとフラグが得られます。
$ echo 9JzMjNTaQ91MMJjMVB3ejNHZ | rev | base64 -d ; echo
dsc{pU22L3_Pi3c32}
Flag: dsc{pU22L3_Pi3c32}
ちなみにですが、Base64、Base16、Base85、reverse、などのもろもろのデコードをまとめてやる自作ツールがあって、実際のところはそれを使って解きました。
Author CaptureAmerica @ CTF フラxxグゲット
LastMod 2021-10-06
