flagCTF Writeup
Contents
URL: http://flagctf.com/
Packer Captureの問題があったのがよかったです。
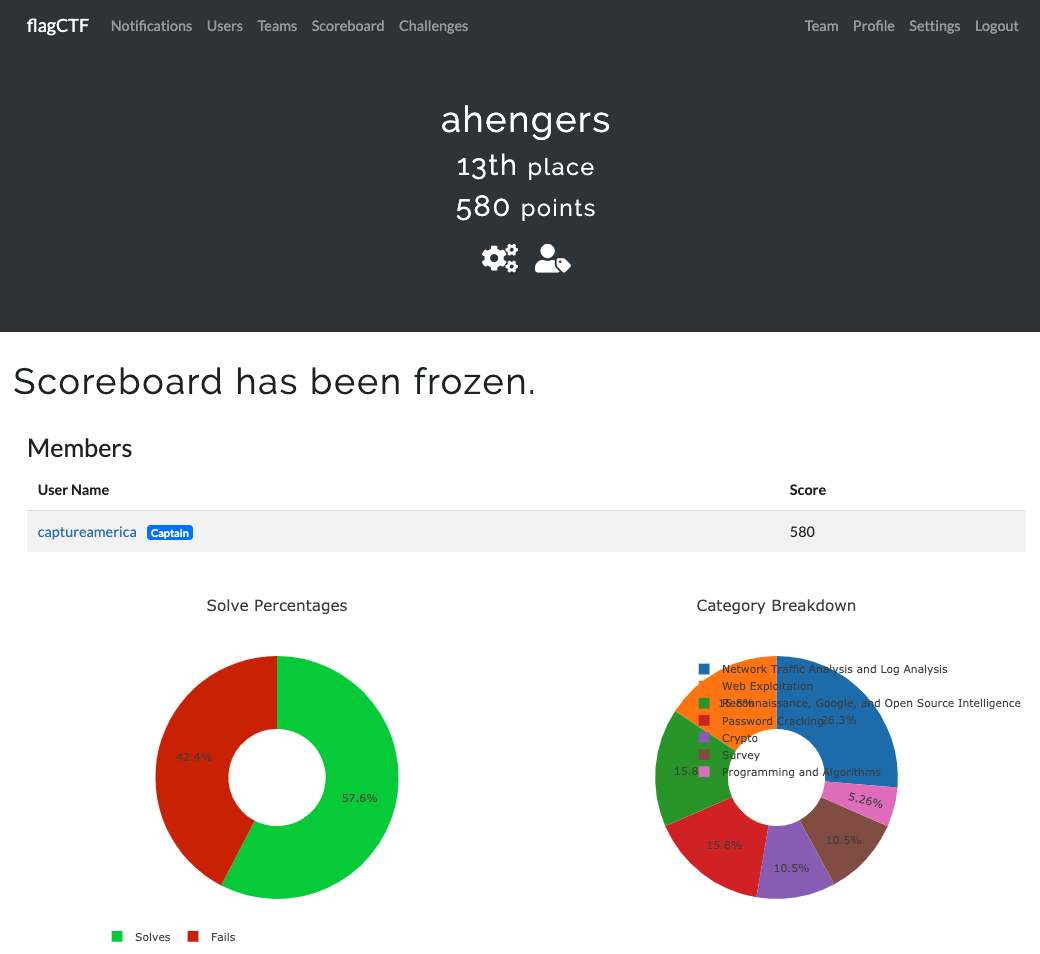
順位が13位で一見成績が良かったように見えますけど、参加者は100人くらいでした。
[Network]: Web Search Packet Capture Q5 (30)
Challenge
The user searched for some queries more times than others. Out of all the queries which are tied for 1st place in number of times searched, which one is last alphabetically?
Note: your team is limited to 6 attempts on this challenge.
Attachment:
- WebSearchingFlagCTF2019.pcapng (Q1 ~ Q5で共通)
Solution
$ tshark -r WebSearchingFlagCTF2019.pcapng | grep -i "search/?" | tail -n 1 4891 82.558070239 192.168.52.110 → 23.10.112.128 HTTP 149 GET /search/?q=auyyxxriyf HTTP/1.1 $ tshark -r WebSearchingFlagCTF2019.pcapng | grep -i "search/?" | cut -d= -f2 | sort | uniq -c | egrep "^ 4" | sort -k 2 4 afqyhedslp HTTP/1.1 4 bnvfsywbnx HTTP/1.1 4 czlhbopugw HTTP/1.1 4 faxuzyzwfl HTTP/1.1 4 onphdplbbx HTTP/1.1 4 ouaxyqrnjz HTTP/1.1
Flag: ouaxyqrnjz
Tips
uniq -cは、重複した行数を表示するオプションです。
[Password Cracking]: Cracking #1 ~ #7
Challenge
Agents have captured password hashes from the hackers in the black-hat group “1337 Hax0r T3am”. We know that they think they are 1337 but they don’t like to use symbols after the words at the base of their passwords, because they heard “Password1!” was a bad password without understanding why. They are known to share a similar interest outside of computers, which may be reflected in their passwords. Note: some of these passwords are unlikely to be found verbatim in password cracking lists or in lists on the internet. It will be necessary to construct wordlists once you find out what the theme is, and extend the wordlists that you find to create longer sensible phrases that might be used as the base of passwords.
Hint: use password cracking software such as hashcat, or john the ripper, to try many possible combinations at once. without a GPU, it can be done in under 1 hour on a decent processor. Hint: start w ith lower entropy, and think how longer passwords might be constructed specific to terms in this domain (field).
Do not brute-force attempt against the website (here), or that will result in a ban. For this set of challenges, you should be sure when you arrived at the answer.
Stay tuned for the video posted at 7:30 pm ET if you’re new to the process as we show how to crack the first hash in this series.
以下は、Cracking #6 (50)より。
The original hash given was: a23b2583b0f977bf3d41ff546f67f13c After there were no solves in the sprint round, you can also crack this hash where the variation of the password contains only lowercase letters: 9cd2a2568ed7d991fb8d2eb1e7e1c7ec
Solution
いくつかは、rainbow tableでcrackできます。
https://crackstation.net/
53b45bbef61cb7ed537d14b1257545d5 : chick3n
005d05de29487ec44cd07bd9d757d4e1 : carrot
2a3555ff38f17a69009fc8da52330f54 : peasandcarrots
残り
ca1443c1c17cbc96d0ae8fa4bd0e2bba
7153a339468b43cd819123708567e3d1
a23b2583b0f977bf3d41ff546f67f13c
9cd2a2568ed7d991fb8d2eb1e7e1c7ec
dc098cc7aadabcffbf1264af50b33027
すでにわかっている3つ(chick3n, carrot, peasandcarrots)より、以下の傾向がわかります。
- 食べ物の単語
- Leetを使用
https://ja.wikipedia.org/wiki/Leet
https://en.wikipedia.org/wiki/Leet - 複数形のsが付いたりする
- まず、Webから食べ物の英単語をかき集めました。
- 以下のツールを使わせてもらい、Leetのバリエーションを使って辞書を強化。
https://github.com/madglory/permute_wordlist - Hashcat実行。
$ hashcat -m 0 -a 0 hash.txt my_food_dic.txt
さっぱりダメでした。。。orz
[Programming]: ME! (45)
Challenge
“You can’t spell ‘awesome’ without ‘me’!” – Taylor Swift/Brendon Urie, “ME!” (2019)
Even with all that you hear in pop songs these days, that is a true statement! You wonder how many words are spelled with the letters ’m’ and ‘e’ in that order, but not necessarily consecutive.
You are given a list of words, and must determine how many satisfy this property.
Input format:
The first line contains the integer N (1 <= N <= 1000), the number of lines to follow. Each of the subsequent N lines contains one of the words in question. The length of each word is at most 500,000 characters. They are not guaranteed to be English words, or words in any language.
Output format: One line, containing the number of words that satisfy that property.
Example input:
5
awesome
lime
mine
eminem
emotion
Example output:
4
Output description:
The first 4 of the 5 words given satisfy that property. The words ‘awesome’ and ‘me’ are clear. In ‘mine’, the letters are not consecutive, and in ‘eminem’, we can use the first ’m’ and the second ‘e’. However, the only ‘e’ in the fifth word, ‘emotion’ is before the ’m’, so this does not count.
Flag format:
Submit the answers for all 5 input files in order, delimited by semicolons. For example, “4;902;489;103;670”.
Attachment:
- me_template.py
- me_inputs_small.zip
Solution
ご親切にPythonのテンプレートが添付されていましたが、コマンドの組み合わせで解きました。
~/me_inputs_small $ for i in {1..5} ; do grep -e ".*m.*e.*" $i.in | wc -l ; done
4
957
245
0
440
Flag 4;957;245;0;440
[Web]: Exquisifax Admin Panel (40)
Challenge
Let’s go back to the Exquisifax site: http://18.217.184.75:8002/. Find a way to log in to the site, and report the flag.
Scope of attack: http://18.217.184.75:8002/*
Solution
ページにアクセスすると、3つのボックスと、Loginページへのリンクがあります。
試しに、ボックスにa、b、cを入れてsubmitすると、以下のエラーが返ってきました。
Warning: readfile(a/c/b): failed to open stream: No such file or directory in /var/www/html/display2.php on line 3
こんな感じで、/var/www/html/login.phpを取りに行きます。
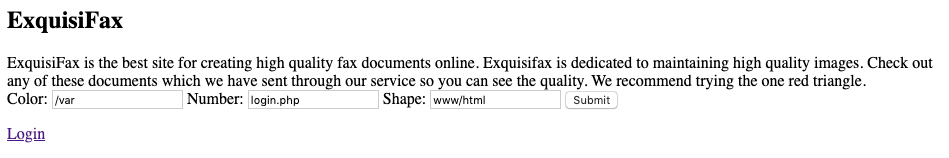
その後、View Page Sourceでphpの中身を見ると、adminパスワードがわかります。
|
|
あとは、ログインページより、ログインするだけです。
Flag: 200aaa7c1acbd70d2b243bbdc761fc38
Author CaptureAmerica @ CTF フラxxグゲット
LastMod 2019-06-16
